Zero Trust Architecture is the emerging security framework that flips traditional security models on their heads. Imagine a world where trust is a rare currency, and every access request undergoes rigorous scrutiny—this is the essence of Zero Trust. As cyber threats become increasingly sophisticated and pervasive, organizations must adapt to safeguard their digital landscapes. This innovative approach not only protects sensitive data but also enhances overall security posture by implementing strict verification processes at every level.
At its core, Zero Trust embodies the principle of “never trust, always verify,” revolutionizing how businesses approach security. Unlike traditional models that rely on perimeter defenses, Zero Trust assumes that threats can emerge from anywhere, whether inside or outside the organization’s network. This paradigm shift encourages a comprehensive understanding of vulnerabilities and emphasizes the need for identity verification, access controls, and continuous monitoring. As we delve deeper, we will explore its fundamental components, implementation strategies, and real-world applications that showcase its transformative potential in today’s cybersecurity landscape.
Understanding the Concept of Zero Trust Architecture
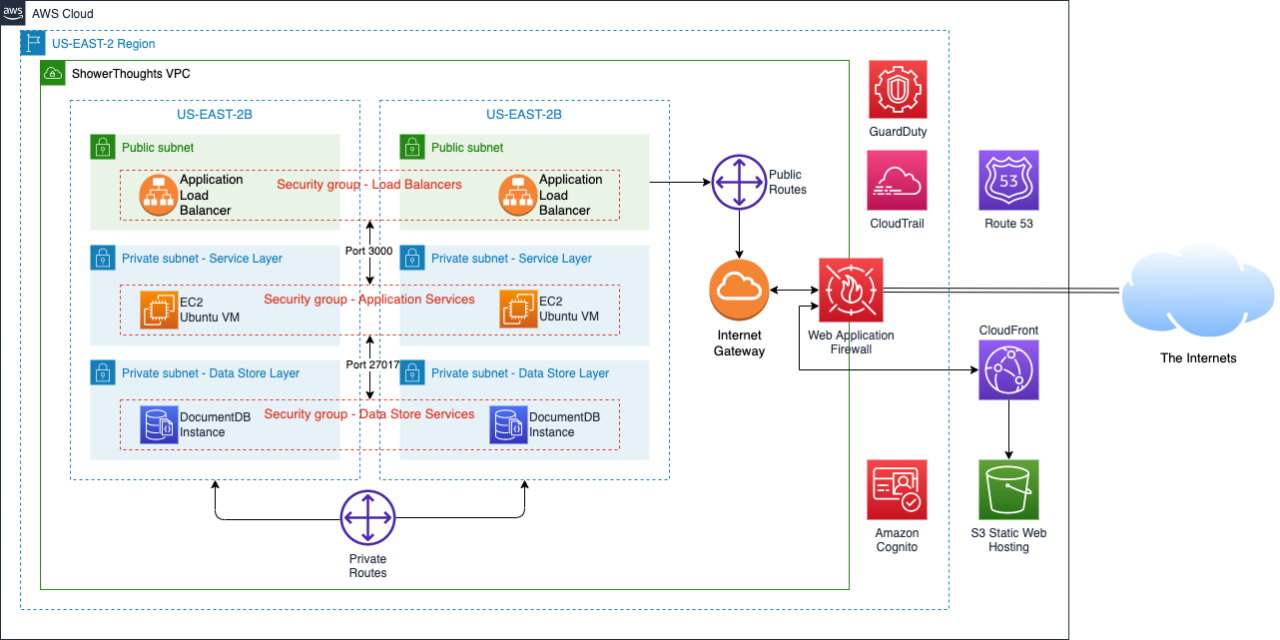
Zero Trust Architecture (ZTA) represents a transformative shift in cybersecurity strategy aimed at mitigating risks associated with increasingly complex digital environments. As organizations grapple with sophisticated cyber threats, traditional perimeter-based security models have proven insufficient. ZTA proposes a fundamental change in approach, whereby security is not only about building strong perimeters but also about assuming that threats can originate from both outside and inside the network. This paradigm shift signifies a commitment to a more proactive security posture, where verification is integral to every access request, regardless of the user’s location or the device being used.
The essence of Zero Trust is encapsulated in its core principle: “never trust, always verify.” In practice, this means that every user, device, and application must be authenticated and authorized before being granted access to any resources. Unlike traditional models that trust users inside the network implicitly, ZTA operates on the assumption that threats can exist everywhere. This approach necessitates a comprehensive understanding of the assets, users, and devices within an organization, allowing for tailored security measures that address specific risks. Furthermore, ZTA leverages technologies such as identity and access management (IAM), multi-factor authentication (MFA), and micro-segmentation to create a robust security framework that dynamically adjusts to evolving threats.
Core Principles of Zero Trust Architecture
At the heart of Zero Trust Architecture are several core principles that guide its implementation and effectiveness. These principles form the foundation upon which organizations can build a resilient security posture. Understanding these principles is crucial for organizations looking to transition to a Zero Trust model.
- Never Trust, Always Verify: This principle emphasizes the need for constant verification of users and devices before granting access to resources. Trust is never assumed based solely on location or previous authentication.
- Least Privilege Access: Users and devices should only be granted the minimum level of access necessary to perform their functions. This limits potential damage in the event of a breach.
- Micro-Segmentation: The network is divided into smaller segments, each with its own security controls. This limits lateral movement within the network and enhances overall security.
- Continuous Monitoring: Organizations must continuously monitor user activities and network traffic to detect and respond to anomalies in real-time.
- Device Security: All devices accessing the network must meet security standards. This includes ensuring that endpoints are compliant with security policies before they can access resources.
Understanding the critical differences between traditional network security models and Zero Trust Architecture is essential for organizations aiming to strengthen their security frameworks. Traditional models typically rely on a strong perimeter defense, trusting users and devices within the network while focusing on external threats. In contrast, Zero Trust assumes that threats can come from anywhere and mandates verification for every access request, regardless of where it originates.
Specifically, traditional models often fail to account for insider threats and compromised credentials, leading to vulnerabilities. Conversely, Zero Trust employs a granular, identity-centric approach that maintains stringent access controls, making it significantly more effective against contemporary cyber threats. Organizations adopting Zero Trust are better equipped to protect sensitive data and maintain regulatory compliance in an era where data breaches are increasingly common.
The Components of Zero Trust Architecture
Zero Trust Architecture (ZTA) is a security model predicated on the principle of “never trust, always verify.” This approach fundamentally alters the way organizations think about security, emphasizing the need for continuous verification regardless of the location of users or devices. The essential components of Zero Trust Architecture work together to create a robust defense against threats by ensuring that every user, device, and network is constantly validated and assessed.
A comprehensive Zero Trust Architecture consists of several critical components, including identity verification, access controls, and threat detection methods. Identity verification is paramount; it ensures that only authorized users can access sensitive resources. This is achieved through multi-factor authentication (MFA), which requires users to provide multiple forms of identification before gaining access. Access controls further enforce security by defining and managing user permissions granularly, ensuring that individuals have access only to the resources necessary for their roles. Threat detection methods continuously monitor user behavior and network traffic to identify and mitigate potential security breaches in real-time.
Identity Verification
Identity verification is the cornerstone of Zero Trust Architecture. To effectively implement this component, organizations utilize various technologies and tools that may include:
- Multi-Factor Authentication (MFA): Requires users to provide two or more verification factors to access systems.
- Single Sign-On (SSO): Streamlines the login process by allowing users to access multiple applications with one set of credentials.
- Identity and Access Management (IAM) solutions: Manage user identities and govern access across various platforms.
Access Controls
Access controls determine who can access what within an organization. They are vital for enforcing security policies based on user roles and responsibilities. Key technologies and tools used for access controls include:
- Role-Based Access Control (RBAC): Assigns permissions based on user roles within the organization.
- Attribute-Based Access Control (ABAC): Utilizes various attributes (user, resource, environment) to make access decisions.
- Privileged Access Management (PAM): Manages and monitors accounts with elevated access privileges to reduce the risk of insider threats.
Threat Detection Methods
Effective threat detection is crucial for a proactive security posture. Various methods and tools are employed to identify and respond to security threats, including:
- Security Information and Event Management (SIEM) systems: Collect and analyze security data from across the organization to detect anomalies.
- Endpoint Detection and Response (EDR): Monitors endpoint devices for suspicious activities and responds to potential threats.
- Network Traffic Analysis tools: Analyze network traffic patterns to identify unauthorized access or data exfiltration.
The roles and responsibilities of each component within Zero Trust Architecture contribute to a cohesive security strategy. By integrating these components, organizations can create a resilient defense against evolving cyber threats and protect their critical assets effectively.
Implementing Zero Trust Architecture in Organizations
Transitioning to a Zero Trust Architecture (ZTA) requires a strategic and methodical approach. Organizations must shift from a traditional security perimeter model to one where trust is never assumed, regardless of the network location. This transition involves a comprehensive understanding of current assets, potential vulnerabilities, and the implementation of robust security measures tailored to individual user needs and behaviors.
The steps toward implementing Zero Trust can be divided into planning, deployment, and ongoing management. Organizations should first conduct a thorough assessment of their existing infrastructure and security protocols. This involves identifying critical assets, mapping data flows, and understanding user behaviors to establish a baseline for security policies. Once the assessment is complete, organizations can begin to deploy technologies that support the Zero Trust model, such as identity and access management (IAM), micro-segmentation, and continuous monitoring. Ongoing management entails regularly updating policies and security measures to adapt to evolving threats and ensuring compliance with industry standards.
Best Practices for Implementing Zero Trust Architecture
Adopting Zero Trust effectively requires adherence to certain best practices that enhance security and streamline the transition process. Below is a table highlighting these practices:
| Best Practice | Description |
|---|---|
| Risk Assessment | Conduct regular assessments to identify vulnerabilities and prioritize security measures based on risk levels. |
| User Identity Verification | Implement strong identity verification methods such as multi-factor authentication (MFA) to ensure only authorized users can access systems. |
| Micro-Segmentation | Divide networks into smaller, isolated segments to minimize lateral movement of threats within the organization. |
| Continuous Monitoring | Utilize real-time monitoring tools to detect and respond to suspicious activities or anomalies as they occur. |
| Least Privilege Access | Enforce policies that grant users the minimum level of access necessary to perform their job functions. |
| Regular Policy Review | Continuously review and update security policies to adapt to new threats and changes in the business environment. |
Organizations face several challenges when implementing Zero Trust. One of the primary obstacles is the resistance to change from employees who are accustomed to traditional security models. To overcome this, organizations should invest in training and awareness programs that clearly explain the benefits of Zero Trust and how it enhances overall security.
Another challenge is the complexity of existing IT environments, which may hinder the seamless integration of Zero Trust principles. To address this, organizations should consider phased implementations, starting with high-risk areas and gradually extending Zero Trust practices across the entire network. Additionally, budget constraints can limit the adoption of necessary technologies. A thorough cost-benefit analysis can help justify investments in Zero Trust solutions by highlighting long-term security benefits and potential cost savings from avoiding breaches.
Transitioning to a Zero Trust Architecture is not just a technical shift; it’s a cultural change that requires commitment from all levels of the organization.
The Role of Identity and Access Management in Zero Trust
Identity and Access Management (IAM) is a foundational pillar of Zero Trust Architecture, playing a vital role in ensuring that only authenticated and authorized users can access sensitive resources. Within a Zero Trust framework, every user and device is treated as a potential threat, necessitating rigorous identity verification and continuous monitoring of access rights. This proactive approach to security not only helps to mitigate the risk of insider threats but also safeguards against external attacks.
IAM facilitates the implementation of the principle of least privilege, which is crucial in a Zero Trust environment. By restricting user access based on their specific roles and responsibilities, organizations can minimize the attack surface significantly. In contrast to traditional identity management systems that often rely on static credentials and perimeter-based security, Zero Trust IAM systems incorporate dynamic policies that adapt to real-time risk assessments and contextual information.
Comparison of Traditional and Zero Trust Identity Management Systems
Traditional identity management systems typically focus on establishing a secure perimeter around the network, relying on established user identities and static access controls. This approach can lead to vulnerabilities, as once users breach the perimeter, they might gain unrestricted access to various resources. In contrast, Zero Trust IAM systems emphasize a continuous verification process, demanding that every access request be authenticated, authorized, and encrypted, regardless of the network location.
Some key differences between traditional and Zero Trust IAM systems include:
- Access Control: Traditional systems often employ role-based access control (RBAC), whereas Zero Trust utilizes attribute-based access control (ABAC) and risk-based access control, considering context and user behavior.
- Authentication Methods: Traditional systems may rely on passwords and single-factor authentication, while Zero Trust typically implements multi-factor authentication (MFA) to enhance security.
- Monitoring and Analytics: Traditional IAM systems may have limited visibility into user activity, while Zero Trust employs continuous monitoring and behavioral analytics to detect anomalies in real-time.
Identity Verification Methods in Zero Trust Framework
Effective identity verification is essential in a Zero Trust framework. Organizations deploy various methods to ensure that users are who they claim to be. Here are some commonly used identity verification methods:
- Multi-Factor Authentication (MFA): This method requires users to provide two or more verification factors, such as a password, a text message code, or biometric data. MFA significantly reduces the risk of unauthorized access.
- Biometric Verification: Techniques like fingerprint scanning, facial recognition, and voice recognition offer a high level of assurance regarding user identity by leveraging unique physical traits.
- Behavioral Analytics: This approach analyzes patterns of user behavior and access to identify any deviations that could indicate compromised accounts or malicious activity.
- Contextual Authentication: This method assesses the context of access requests, including location, device security status, and time of access, to determine whether to grant or deny access.
“In a Zero Trust model, trust is never assumed and always verified.”
Zero Trust Architecture and Cloud Security
Zero Trust Architecture (ZTA) fundamentally reshapes how organizations approach cloud security. With the rapid adoption of cloud services, organizations are increasingly recognizing that traditional perimeter-based security models are no longer sufficient. ZTA emphasizes that trust should not be implicit based on location or network. Instead, it advocates for continuous verification of user identities, device integrity, and contextual access, creating a more resilient security posture against the dynamic threats present in cloud environments.
Implementing Zero Trust in cloud security is not just a trend; it has become a necessity as organizations migrate sensitive data and workloads to the cloud. This approach helps organizations mitigate several inherent security challenges posed by cloud environments, such as the following:
Security Challenges in Cloud Environments Addressed by Zero Trust
Cloud environments present unique security challenges that can jeopardize sensitive data and operations. The integration of Zero Trust principles can effectively address these issues:
1. Data Breaches: Traditional security models often leave data vulnerable after it has been accessed. Zero Trust ensures that access to data is continuously monitored and controlled, minimizing the risk of breaches.
2. Insecure Interfaces and APIs: Cloud services rely heavily on APIs, which can be exploited if not properly secured. Zero Trust mandates strict authentication and authorization protocols for all API interactions.
3. Insider Threats: Employees or contractors with legitimate access can pose significant risks. By applying Zero Trust, organizations can limit user access based on the principle of least privilege, reducing potential misuse.
4. Shadow IT: Employees may use unauthorized cloud services that are not monitored or protected. Zero Trust frameworks can help identify and mitigate the risks associated with shadow IT by enforcing policies and visibility across all applications in use.
5. Multi-Cloud Complexity: Organizations often use multiple cloud providers, leading to increased complexity in security management. Zero Trust provides a unified approach, ensuring consistent security policies across various environments.
“The integration of Zero Trust principles in cloud security strategies empowers organizations to safeguard their data and applications by ensuring that trust is never assumed, but always verified.”
By adopting Zero Trust Architecture, organizations can significantly enhance their cloud security posture. This proactive approach not only protects against external attacks but also fortifies defenses against internal vulnerabilities, ensuring that both data and resources are secured throughout their lifecycle in the cloud.
Zero Trust Architecture: A Future Perspective
The future of Zero Trust Architecture (ZTA) is poised to redefine the landscape of cybersecurity. As organizations increasingly transition to digital operations, the traditional security perimeter is becoming obsolete. ZTA offers a comprehensive framework that assumes threats can originate from both outside and within the network. This perspective fosters a more proactive approach to security, prioritizing continuous verification and least-privilege access to safeguard sensitive data and systems.
Emerging trends and technologies are significantly shaping the evolution of Zero Trust frameworks. First among these is the integration of artificial intelligence (AI) and machine learning (ML) into security systems. These technologies can enhance threat detection and response capabilities by analyzing vast amounts of data in real time. For instance, AI can identify unusual patterns in user behavior, flagging potential security breaches before they escalate. Additionally, advancements in identity and access management (IAM) solutions enable organizations to implement more robust authentication methods, such as biometric verification, enhancing user identity verification processes.
Another key trend influencing ZTA is the rapid adoption of cloud services. As businesses migrate to the cloud, they face unique security challenges that necessitate the implementation of Zero Trust principles. The need to secure data across various cloud environments while ensuring seamless access for users is driving the development of dynamic security policies that adapt to changing circumstances. Multi-cloud strategies are also on the rise, requiring more intricate Zero Trust frameworks that can manage diverse security needs across multiple service providers.
Regulatory changes are another critical factor affecting the adoption of Zero Trust Architecture. As data privacy laws tighten globally, organizations are compelled to reevaluate their security protocols to comply with regulations such as GDPR and CCPA. These regulations mandate stricter controls over data access and management, making Zero Trust a practical and necessary approach. Compliance not only mitigates the risk of penalties but also strengthens the overall security posture of organizations, fostering greater trust among customers and stakeholders.
In summary, as the cybersecurity landscape continues to evolve, Zero Trust Architecture will play a pivotal role in shaping effective security strategies. The convergence of emerging technologies, the shift to cloud operations, and the influence of regulatory frameworks will collectively drive the need for robust Zero Trust implementations, ensuring security remains a top priority in an increasingly complex digital world.
Real-World Case Studies of Zero Trust Implementation
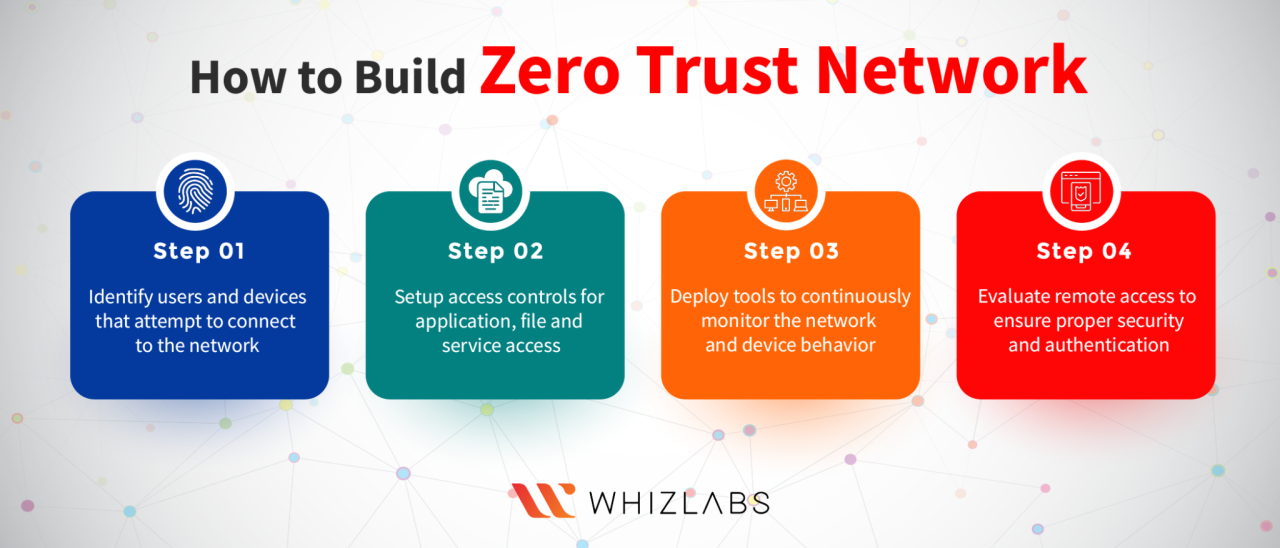
Organizations across various sectors have increasingly adopted Zero Trust Architecture (ZTA) to bolster their cybersecurity posture. By shifting from traditional perimeter-based security models to a zero-trust approach, these organizations have mitigated risks related to data breaches and insider threats. The following case studies showcase successful implementations of ZTA, illustrating their strategies, outcomes, and lessons learned.
Case Studies Across Different Sectors
Several organizations have set benchmarks in Zero Trust implementation, employing varied strategies tailored to their unique challenges. Here’s a look at a few notable examples:
1. Financial Services Sector: A Major Bank
A leading global bank adopted Zero Trust to enhance its protection against cyber threats. The strategy involved deploying identity and access management (IAM) tools to enforce strict authentication protocols. Additionally, the bank segmented its network into smaller zones to limit lateral movement. The result was a significant reduction in unauthorized access attempts, with the bank reporting a decrease of nearly 40% in security incidents within the first year of implementation.
2. Healthcare Sector: A Large Hospital Network
A major hospital network implemented Zero Trust to safeguard patient data amidst increasing cyber-attacks targeting healthcare institutions. Their approach included continuous monitoring of user behavior and implementing multi-factor authentication across all access points. Consequently, the hospital network experienced a marked improvement in its incident response times and successfully thwarted a potential data breach that could have compromised thousands of patient records.
3. Technology Sector: A Leading Software Company
A prominent software company turned to Zero Trust as part of its digital transformation strategy. By integrating automated security protocols and real-time risk assessment tools, the company ensured that only authorized users could access critical systems. This proactive stance not only enhanced security measures but also fostered greater employee confidence in the company’s commitment to protecting sensitive information. The company noted a 50% reduction in compliance-related incidents within six months of implementing the zero-trust model.
Lessons Learned and Best Practices
Implementing Zero Trust Architecture offers crucial insights and best practices that can benefit other organizations considering this approach. Key takeaways from the aforementioned case studies include:
– Emphasize Identity Verification: Continuous and rigorous identity verification processes are vital, as they ensure that only authorized personnel can access sensitive data.
– Micro-Segmentation is Key: Dividing networks into smaller, manageable segments limits the potential for lateral movement by attackers, thereby enhancing overall security.
– Invest in Automation: Automated security solutions that provide real-time monitoring and alerts can significantly improve incident response times and reduce human error.
These case studies illustrate that regardless of the sector, the adoption of Zero Trust Architecture empowers organizations to address modern security challenges effectively. As the digital landscape continues to evolve, the principles of Zero Trust will remain instrumental in fortifying defenses against sophisticated cyber threats.
Summary
In conclusion, Zero Trust Architecture presents a robust framework for addressing the evolving threats faced by modern organizations. By emphasizing a mindset of constant verification and adapting to emerging technologies, companies can significantly mitigate risks and enhance their resilience against cyberattacks. As we have seen through various case studies and discussions, the journey toward implementing Zero Trust is not without challenges, but the rewards in terms of security assurance and peace of mind are well worth the effort. Embracing this approach will not only fortify defenses but also pave the way for a more secure digital future.
Helpful Answers
What is the main goal of Zero Trust Architecture?
The primary goal is to minimize security risks by ensuring that no one is trusted by default, regardless of their location, and that they must continuously verify their identity and access rights.
How does Zero Trust Architecture differ from traditional security?
Unlike traditional security that focuses on securing perimeters, Zero Trust assumes that threats can come from anywhere and requires verification for every access request, both inside and outside the network.
What are the key components of Zero Trust Architecture?
Key components include identity verification, access controls, device security, network segmentation, and continuous monitoring to ensure compliance and detect threats.
Can Zero Trust be implemented in existing IT environments?
Yes, Zero Trust can be integrated into existing IT infrastructures, although it may require a phased approach to gradually align with Zero Trust principles.
What role does identity management play in Zero Trust?
Identity management is crucial in Zero Trust, as it ensures that only authenticated and authorized users can access resources, thereby reducing the risk of unauthorized access.