Virtual Private Network (VPN) sets the stage for this enthralling narrative, offering readers a glimpse into a story that is rich in detail and brimming with originality from the outset. Imagine a digital realm where your online activities are shrouded in privacy, and your data is safeguarded from prying eyes. A VPN provides that sanctuary, creating a secure tunnel for your internet traffic while masking your IP address.
This technology is not just a luxury for tech enthusiasts; it’s a vital tool for anyone seeking enhanced security and privacy online. Whether you’re working from home, connecting to public Wi-Fi, or accessing restricted content, a VPN serves as your shield against threats and limitations. It empowers users to navigate the internet more freely and safely, making it an essential resource in our increasingly digital world.
Understanding the Basics of Virtual Private Networks
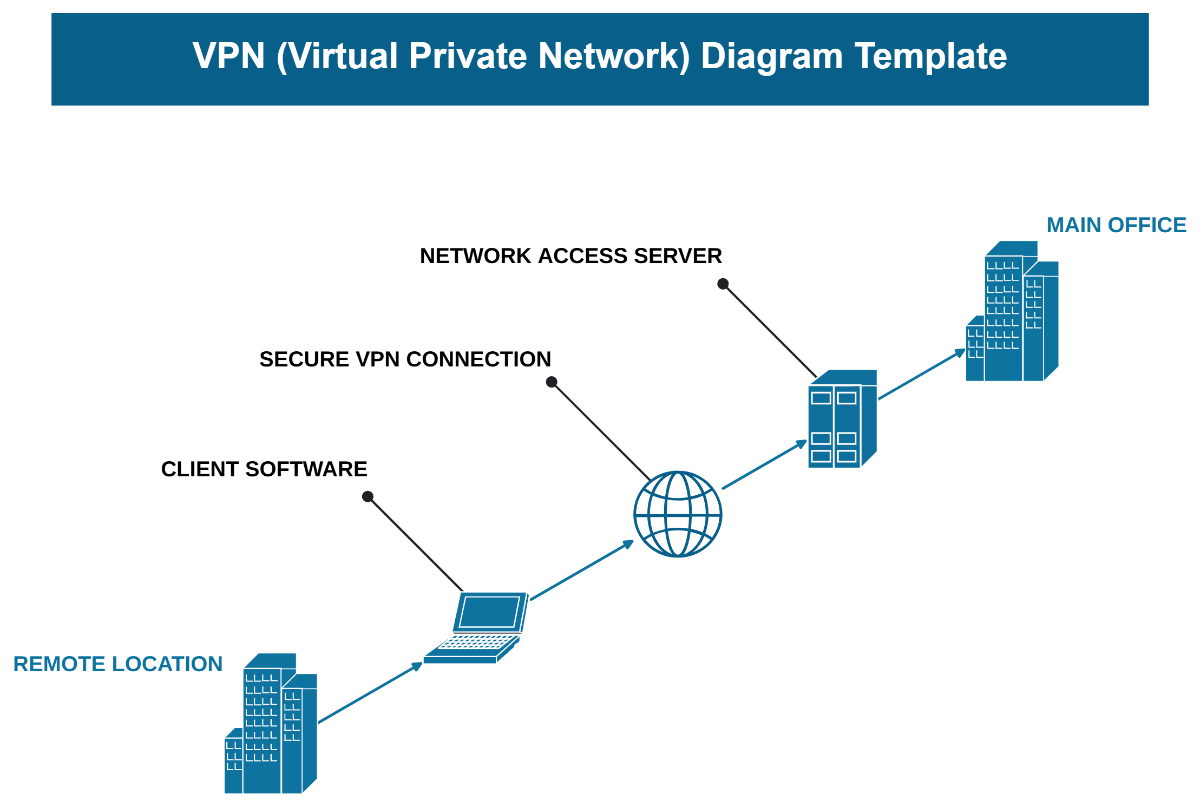
Virtual Private Networks (VPNs) have evolved into an essential tool for enhancing online privacy and security in today’s digital landscape. A VPN establishes a secure connection over the internet, allowing users to send and receive data as if they were directly connected to a private network. This process is facilitated through the use of encryption and tunneling protocols, which create a safe channel for data transfer. When a device connects to a VPN, it is assigned an IP address from the VPN server, effectively masking the user’s real IP address and location, thereby enhancing their anonymity online.
The primary purposes of using a VPN revolve around privacy and security. By encrypting internet traffic, VPNs protect sensitive information, such as personal data, financial transactions, and browsing activities, from potential interception by hackers and cybercriminals. This is particularly important when using unsecured networks, such as public Wi-Fi, which are often targeted for data theft. Additionally, VPNs allow users to bypass geographical restrictions on content, enabling access to services that may be blocked in certain regions, all while maintaining a level of privacy.
Utilization of VPNs in Various Scenarios
VPNs are utilized in a multitude of scenarios, reflecting their versatility in enhancing both privacy and security. Here are some prominent examples:
- Remote Work: With the increase in remote work, many companies implement VPNs to provide their employees secure access to the company’s internal network. This ensures that sensitive company data remains protected while allowing employees to work from anywhere.
- Public Wi-Fi Security: Using a VPN in public spaces, such as cafes or airports, is crucial. It safeguards users against potential threats like data snooping, ensuring their online activities and personal information remain confidential.
- Bypassing Geographic Restrictions: VPNs enable users to access content that may be restricted based on their geographical location, such as streaming services or websites that are only available in certain countries.
- Anonymity for Online Activities: Users concerned about their online footprint utilize VPNs to obscure their internet activity from ISPs and other entities, enhancing their overall privacy.
“VPNs provide a vital layer of security, especially in an era where data breaches and online surveillance are increasingly common.”
The Technology Behind VPNs
Virtual Private Networks (VPNs) utilize various technologies to create secure connections over the internet, safeguarding user data and maintaining privacy. Understanding these technologies, particularly the protocols that govern them, is crucial for selecting the right VPN service. The most common protocols include OpenVPN, L2TP, and IPSec, each with its unique features, benefits, and potential limitations.
VPN Protocols Overview
The choice of VPN protocol significantly affects both the security of the connection and the performance experienced by the user. Here’s a breakdown of three of the most widely used protocols:
- OpenVPN: OpenVPN is an open-source protocol that is highly configurable and uses SSL/TLS for encryption. It’s recognized for its strong security features, supporting up to 256-bit encryption keys. OpenVPN is versatile and can work over both TCP and UDP, which makes it suitable for various network conditions. Its use of encryption standards like AES (Advanced Encryption Standard) contributes to its reputation for safety.
- L2TP/IPSec: Layer 2 Tunneling Protocol (L2TP) is often paired with IPSec to provide encryption. While L2TP itself does not provide encryption, combining it with IPSec ensures a secure tunnel for data transfer. This protocol is reliable and provides confidentiality, integrity, and authentication. However, L2TP/IPSec can be slower due to double encapsulation of data.
- IPSec: Internet Protocol Security (IPSec) is a suite of protocols that encrypts IP packets at the network layer. It can operate in two modes: transport mode and tunnel mode. IPSec is often used to secure L2TP and is known for its robust security features, including Authentication Header (AH) for integrity and Encapsulating Security Payload (ESP) for confidentiality.
The choice of protocol influences not only the security of a VPN connection but also the user experience. For instance, while OpenVPN provides excellent security and flexibility, it may require more resources, which can affect performance. On the other hand, L2TP/IPSec might introduce noticeable latency due to its encapsulation process, making it less desirable for high-speed applications.
Importance of Encryption in VPNs
Encryption plays a pivotal role in VPN technology, ensuring that data transmitted over virtual private networks remains confidential and secure from prying eyes. The encryption process encodes data so that even if it is intercepted, unauthorized individuals cannot read it.
- AES (Advanced Encryption Standard): Widely regarded as one of the most secure encryption standards, AES is utilized by many VPN providers. It supports key sizes of 128, 192, and 256 bits, with 256-bit AES being the standard for high-security applications. For example, the U.S. government uses AES for encrypting sensitive information.
- RSA (Rivest-Shamir-Adleman): RSA is a widely used public-key encryption method that enables secure data transmission. It is commonly used in the key exchange process of VPNs to establish a secure channel before data transfer begins.
- ChaCha20: An alternative to AES, ChaCha20 is gaining adoption due to its efficiency on mobile devices and its strong security capabilities. It offers high-speed performance while maintaining robust encryption, making it suitable for environments where performance is critical.
In summary, the technology behind VPNs is complex and multifaceted, rooted in a variety of protocols and encryption methods that work together to secure digital communications. The right combination can significantly enhance privacy and user experience, while poor choices may expose users to risks. By understanding these elements, individuals can make informed decisions about their VPN options and enhance their online security effectively.
Choosing the Right VPN Service

When it comes to selecting a Virtual Private Network (VPN) service provider, the choices can be overwhelming. With the increasing demand for online privacy and security, a variety of VPNs have emerged, each offering different features and pricing structures. Understanding the key factors that influence your decision can lead to a more satisfactory choice tailored to your needs.
The importance of a reliable VPN service cannot be overstated. Key factors such as speed, reliability, security features, and customer support should be assessed carefully to ensure that the service you choose meets your specific requirements. Here’s a breakdown of essential elements to consider when making your selection.
Essential Factors to Consider
Choosing the right VPN provider requires a careful look at specific features that can impact your overall experience. Below are crucial aspects to consider:
- Speed: A fast connection is vital for streaming, gaming, and browsing without interruptions. Look for providers offering high-speed servers in multiple locations.
- Reliability: Consistent uptime and a robust infrastructure are important for uninterrupted service. Check the provider’s track record for reliability.
- Security Features: Look for features such as strong encryption protocols, a no-logs policy, and advanced security measures like kill switches and DNS leak protection.
- Customer Support: Responsive customer service can save you time and frustration. Ensure they offer multiple support channels, such as live chat, email, and a comprehensive knowledge base.
- Pricing: Assess the value offered by the monthly or yearly subscription plans, including any potential money-back guarantees or free trials.
To help visualize the differences among popular VPN providers, the table below compares key features, pricing, and user reviews:
| VPN Provider | Features | Price (Monthly) | User Rating |
|---|---|---|---|
| ExpressVPN | High speed, Secure encryption, Split tunneling | $12.95 | 4.7/5 |
| NordVPN | Double VPN, CyberSec, P2P support | $11.95 | 4.6/5 |
| Surfshark | Unlimited devices, CleanWeb, MultiHop | $12.95 | 4.5/5 |
| CyberGhost | User-friendly, Streaming optimized, Dedicated IP | $12.99 | 4.3/5 |
A personal experience with a VPN service revealed that speed and reliability are often the most valued attributes among users. For instance, during a busy work-from-home period, a VPN that delivered consistent high speeds allowed for smooth video calls and protected online transactions. Meanwhile, having accessible customer support was invaluable when encountering technical issues.
In summary, taking the time to evaluate these factors will greatly enhance your chances of finding the VPN service that best fits your online needs.
Legal and Ethical Considerations of Using a VPN
Using a Virtual Private Network (VPN) can provide users with privacy and security online, but it also comes with a host of legal and ethical considerations that vary across different jurisdictions. Understanding these aspects is crucial for anyone considering VPN usage, ensuring that their online activities remain within legal boundaries while navigating the complex web of internet freedom and accessibility.
Legal Implications of VPN Usage
The legal status of VPNs differs significantly worldwide, with some countries embracing their use while others impose strict regulations or outright bans. Here’s an overview of how various regions approach VPN legality:
- In the United States, VPNs are legal and widely used for privacy protection, although users should be aware of the Terms of Service of websites they access.
- Countries like China and Russia have implemented stringent laws that restrict or prohibit the use of unauthorized VPNs, often requiring government approval for VPN services.
- In many European nations, VPNs are legal and are often used to ensure data protection in compliance with the General Data Protection Regulation (GDPR).
- Countries such as Iran and North Korea impose heavy fines or imprisonment for using VPNs that do not comply with governmental regulations.
The implications of these laws can lead to severe consequences for users who inadvertently violate local regulations, underscoring the importance of understanding the legal landscape in one’s country before using a VPN.
Ethical Considerations in VPN Usage
Using a VPN raises several ethical questions, particularly regarding the potential to bypass geo-restrictions and access blocked content. While the motivations for using a VPN may be legitimate, such as protecting privacy or accessing information, the ethical dilemmas can vary based on user intent:
- Bypassing geo-restrictions often leads to debates about fairness and access to content, especially regarding digital services that employ different pricing models based on location.
- Accessing restricted content in countries with oppressive regimes can be seen as a moral imperative, providing individuals with access to vital information and resources.
- However, using a VPN to partake in activities such as copyright infringement or accessing illegal streaming services raises ethical concerns about contributing to content piracy and theft.
- Users must also consider the potential for abuse of VPNs for cyberbullying, harassment, or other malicious online activities that can have harmful real-world consequences.
The ethical implications highlight the need for responsible VPN usage, weighing personal freedoms against broader societal impacts.
Consequences of Using a VPN for Illicit Activities
While VPNs can provide anonymity, they are not foolproof and can lead to serious consequences if used for illegal activities. Users should be aware of the following potential repercussions:
- Law enforcement agencies are increasingly using advanced technologies to track VPN traffic, meaning illicit activities can still be traced back to individuals.
- Using a VPN to engage in criminal activities, such as hacking or distributing malware, can result in severe legal actions, including fines and imprisonment.
- Service providers may terminate accounts or ban users who violate their terms of service by engaging in illegal practices while using a VPN.
- The false sense of security provided by VPNs can lead individuals to take greater risks online, inadvertently landing them in legal trouble.
Being informed about these consequences is essential for users to navigate the complexities of online privacy and legality effectively.
Common Misconceptions about VPNs
Many users have a skewed perception of what Virtual Private Networks (VPNs) can and cannot do. As VPN technology has gained popularity, misconceptions have proliferated alongside it. Understanding these myths is crucial, as it can enhance user experience and security. Let’s clarify some common misunderstandings surrounding VPNs.
One prevalent myth is that VPNs make users completely anonymous online. While VPNs encrypt user data and mask IP addresses, they do not guarantee complete anonymity. Internet Service Providers (ISPs) and websites can still gather data through other means, such as browser fingerprinting or cookies. Furthermore, the VPN provider itself might log user activity, which could potentially compromise privacy.
Another misconception is that VPNs provide unlimited security. Although VPNs encrypt data and protect connections on public networks, they are not a panacea against all types of cyber threats. Users should still employ strong passwords, keep software updated, and use additional security measures like two-factor authentication. Relying solely on a VPN can create a false sense of security.
Limitations of VPNs
Understanding the limitations of VPNs is essential for users seeking to maximize their benefits. Here are some notable pitfalls to avoid:
The speed of internet connections can be affected by VPN usage. As data is encrypted and routed through a VPN server, users may experience slower speeds. Selecting a high-quality VPN provider with optimized servers can help minimize this issue.
VPNs do not protect against malware and phishing attacks. Users remain vulnerable to these threats unless they employ comprehensive security solutions, such as antivirus software. Relying solely on VPNs for security can lead to significant vulnerabilities.
Not all VPNs are created equal, and some free services can compromise user data. Free VPNs often monetize through advertising or selling user data, which defeats the purpose of using a VPN for privacy. Choosing a reputable, paid VPN service is often more beneficial for maintaining security and privacy.
User testimonials illustrate these misunderstandings effectively. One user reported feeling invincible while using a VPN, only to later find out that their personal information was still leaked due to weak password management. Another case involved a business relying on a free VPN for secure communications, which ultimately led to a data breach, exposing sensitive information. These instances highlight the importance of understanding what a VPN can truly offer and the necessity of complementary security measures.
Future Trends in VPN Technology
The VPN landscape is evolving rapidly, driven by technological advancements and user demands for enhanced security and speed. Emerging trends are shaping how individuals and businesses utilize Virtual Private Networks. As internet usage increases globally, VPNs are becoming essential tools for maintaining privacy and security. This section analyzes the future of VPN technology, focusing on advancements in speed, security, and user interface features, as well as the implications of technologies like 5G and AI.
Technological Advancements Impacting VPNs
The future of VPN technology will see significant enhancements across several dimensions. Speed improvements will be a major trend, particularly with the rollout of 5G technology. 5G offers much higher bandwidth and lower latency, allowing for seamless streaming and faster downloads. Users can expect VPNs to leverage this technology to provide super-fast connections that minimize lag, making it easier to access content globally.
Moreover, security remains a central focus, especially as cyber threats become more sophisticated. Innovations in encryption protocols such as WireGuard are set to replace older technologies, offering faster performance without sacrificing security. This improved encryption can significantly enhance user privacy, as data becomes harder to intercept or decipher.
User interface features will also evolve to enhance the user experience. Future VPN applications are likely to incorporate AI-driven recommendations that automatically connect users to the optimal server based on their location and usage patterns. This can eliminate the guesswork for users who may not be tech-savvy, streamlining the connection process and enhancing overall satisfaction.
The integration of machine learning algorithms will further bolster security measures, enabling VPNs to identify and respond to potential threats in real-time. Over the next decade, we may see VPNs that not only protect user data but also predict and mitigate risks before they materialize.
“Advancements in AI and 5G technology promise to redefine the efficiency and security of VPN services.”
As VPNs evolve, we will also witness a shift in usage patterns from both consumer and corporate perspectives. Consumers will increasingly utilize VPNs for everyday activities like streaming and online shopping, as concerns over privacy and data security grow. For instance, as more people work remotely, having a secure connection to access company resources will be paramount.
On the corporate side, businesses will likely adopt more sophisticated VPN solutions that incorporate not just connectivity but also robust security features. Companies may implement split tunneling to allow employees to access public networks without compromising sensitive internal data. Furthermore, the rise of remote work will push enterprises to invest in VPN solutions that also provide monitoring and analytics, ensuring compliance and enhancing security.
In conclusion, the future of VPN technology is promising, with advancements in speed, security, and user interface features driving the evolution of these essential tools. As new technologies emerge, VPN providers will need to adapt to meet the changing needs of both consumers and businesses.
Final Wrap-Up
In summary, the exploration of Virtual Private Networks (VPN) reveals their crucial role in today’s connected society. As we continue to rely on the internet for both personal and professional activities, understanding the benefits, technologies, and considerations surrounding VPNs becomes imperative. Whether you prioritize security, privacy, or unrestricted access, a well-chosen VPN can significantly enhance your online experience, ensuring that you’re protected in the vast digital landscape.
Clarifying Questions
What is a VPN?
A VPN is a service that creates a secure connection over the internet, allowing users to send and receive data while maintaining privacy and security.
Can I use a VPN on my mobile device?
Yes, most VPN services offer applications for mobile devices, enabling secure browsing on smartphones and tablets.
Will a VPN slow down my internet speed?
While using a VPN may slightly reduce your speed due to encryption, high-quality VPNs often provide fast connections that minimize this impact.
Is using a free VPN safe?
Free VPNs can come with risks such as data logging, ads, and limited security features. It’s often safer to opt for a reputable paid service.
Can a VPN help me access geo-restricted content?
Yes, a VPN allows users to bypass geographic restrictions by connecting to a server in a different location, making it appear as if they are browsing from that region.