Cryptography is an intriguing field that combines mathematics, computer science, and art to secure communication. As we navigate a world increasingly reliant on digital interactions, understanding cryptography’s evolution and its pivotal role in safeguarding our information becomes paramount. From ancient ciphers to modern algorithms, this journey unveils the milestones and innovations that have shaped the way we protect our secrets.
Throughout history, cryptography has experienced significant transformations, driven by the need for privacy and security. This overview will cover key milestones, explore prominent figures who have influenced cryptographic methods, and delve into the essential algorithms that underpin today’s digital security landscape.
The Historical Evolution of Cryptography

The journey of cryptography is a fascinating tale that weaves through time, reflecting the evolving needs for secure communication. From ancient civilizations to modern-day encryption algorithms, cryptographic methods have played an essential role in protecting sensitive information. This historical evolution is marked by significant milestones and influential figures who shaped the field.
One of the earliest known examples of cryptography dates back to ancient Egypt around 1900 BC, where hieroglyphs were used in a coded manner to conceal messages. As civilizations advanced, so did their methods of encrypting information. The Greeks utilized the Scytale, a tool that involved wrapping a strip of parchment around a rod to create a cipher, while the Romans developed the Caesar cipher, which shifted letters in the alphabet to obscure messages. Fast forward to the Middle Ages, where the invention of the polyalphabetic cipher by Leone Battista Alberti marked a major advancement, as it utilized multiple alphabets to increase complexity.
Significant Historical Figures in Cryptography
Several historical figures have made notable contributions to the development of cryptography. Their innovative ideas helped shape the field and paved the way for future advancements.
- Julius Caesar: The Roman general and statesman is well-known for the Caesar cipher, which involved shifting letters in the alphabet by a fixed number. His simple yet effective method laid the groundwork for various substitution ciphers used later.
- Leon Battista Alberti: A true Renaissance man, Alberti introduced the polyalphabetic cipher in the 15th century. This technique allowed for greater security by utilizing multiple cipher alphabets, making it significantly harder to crack than previous methods.
- Augustus de Morgan: A British mathematician in the 19th century, de Morgan contributed to the theoretical underpinnings of cryptography. His work on logical calculations and algebraic structures provided a mathematical foundation for modern cryptographic techniques.
Ancient cryptographic techniques had a profound impact on communication security. For instance, the use of the Atbash cipher, a simple monoalphabetic substitution cipher where letters are reversed, was employed in ancient Hebrew texts. Such methods, while basic by today’s standards, provided a necessary layer of secrecy for military and political communications. This illustrates how ancient societies recognized the value of protecting sensitive information, setting the stage for the sophisticated cryptographic systems we rely on today.
Understanding Modern Cryptographic Algorithms
Cryptography is the backbone of data security in today’s digital landscape. With the increase in cyber threats and the need for secure communication, understanding modern cryptographic algorithms is essential. These algorithms are designed to encrypt data, ensuring confidentiality, integrity, and authentication in various applications, from online banking to secure messaging. The following sections will delve into the most commonly used cryptographic algorithms, explore the distinctions between symmetric and asymmetric encryption, and highlight the significance of hashing functions in cryptography.
Commonly Used Cryptographic Algorithms
Modern cryptographic algorithms can be classified broadly into two categories: symmetric and asymmetric algorithms. Each type has its unique characteristics and applications that make them suitable for specific scenarios.
- AES (Advanced Encryption Standard): AES is a symmetric encryption algorithm widely used across the globe. It supports key sizes of 128, 192, and 256 bits, making it highly secure for protecting sensitive data. It is employed in various applications, including file encryption, secure communications, and data protection in cloud services.
- RSA (Rivest-Shamir-Adleman): RSA is one of the first public-key cryptosystems and remains a cornerstone of secure internet communication. It utilizes two keys: a public key for encryption and a private key for decryption. RSA is often used for secure data transmission and digital signatures.
- ECC (Elliptic Curve Cryptography): ECC offers similar security to RSA but with significantly smaller key sizes, making it more efficient. This algorithm is increasingly used in mobile devices and IoT (Internet of Things) applications due to its lower power consumption.
- SHA-2 (Secure Hash Algorithm 2): SHA-2 is a family of hashing algorithms, including SHA-256 and SHA-512. It is widely used for generating secure cryptographic hashes, which are essential for data integrity verification and digital signatures.
- Blowfish: Blowfish is another symmetric algorithm that operates on 64-bit blocks and supports variable key lengths. It is known for its speed and effectiveness, making it suitable for applications requiring high performance.
Differences Between Symmetric and Asymmetric Encryption
Symmetric and asymmetric encryption serve different purposes in the realm of cryptography. Understanding their differences is crucial for implementing effective security measures.
Symmetric encryption uses a single key for both encryption and decryption. This means that the sender and receiver must share the same key securely. An example of this is AES, which encrypts data efficiently but poses challenges in key distribution. If the key is intercepted, the security of the data is compromised.
In contrast, asymmetric encryption employs a pair of keys: a public key and a private key. The public key can be shared openly, while the private key must be kept confidential. RSA is a common example of asymmetric encryption, allowing users to encrypt messages with the recipient’s public key, which can only be decrypted by the corresponding private key. This method simplifies key management and enhances security but may be slower in processing compared to symmetric encryption.
Role of Hashing Functions in Cryptography
Hashing functions are essential in cryptography for ensuring data integrity and authenticity. They generate a fixed-size output (hash) from input data of any size, making them useful for various applications.
Hashing functions are used in digital signatures, where a hash of the message is created and encrypted with the sender’s private key, allowing the recipient to verify the signature with the sender’s public key. They are also crucial in securing passwords, as only the hash of the password is stored, protecting it from exposure.
Common hashing algorithms include SHA-2, which provides strong security against collision attacks, and MD5, which, while once popular, is now considered insecure for cryptographic purposes. The choice of hashing function is critical for maintaining the security and integrity of data in digital transactions.
The Importance of Cryptography in Cybersecurity
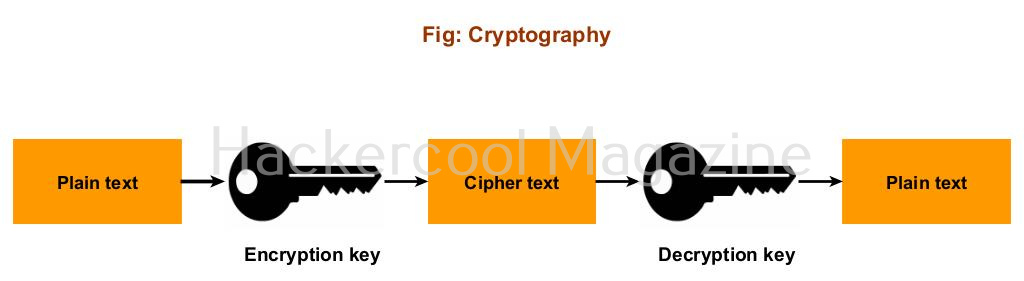
In the digital age, cryptography serves as a vital shield protecting sensitive information from unauthorized access and cyber threats. As individuals and organizations rely more heavily on digital communication and data storage, the necessity for robust cryptographic techniques has never been more pressing. Cryptography not only secures data but also ensures that it remains confidential, integral, and authentic throughout its lifecycle.
The core function of cryptography is to transform readable information into a secure format, rendering it unintelligible to unauthorized users. This transformation is achieved through algorithms that encode data, making it accessible only to those possessing the correct decryption keys. By implementing cryptographic protocols, organizations can protect sensitive data such as personal identification information, financial records, and confidential communications from cybercriminals who may seek to exploit such information for malicious purposes.
Implications of Cryptographic Failures
The ramifications of cryptographic failures can be severe, leading to data breaches that compromise personal and organizational integrity. One glaring example is the 2017 Equifax data breach, where attackers exploited vulnerabilities in the company’s cryptographic practices, leading to the exposure of personal information of over 147 million individuals. This incident not only caused financial losses but also damaged public trust in Equifax and its ability to safeguard sensitive data.
Another notable case is the 2014 Sony Pictures hack, where sensitive corporate data, including unreleased films and employee information, was leaked after attackers gained access through weak cryptographic measures. The fallout included significant reputational damage and financial implications for the company, highlighting how critical effective cryptographic practices are in maintaining cybersecurity.
The need for robust cryptography is underscored by the evolution of cyber threats. As attackers become more sophisticated, organizations must prioritize their cryptographic measures to stay ahead of potential vulnerabilities. This involves not only using stronger encryption algorithms but also regularly updating and auditing existing systems to identify and rectify weaknesses.
To enhance cryptographic practices, organizations can adopt several strategies:
1. Regular Security Audits: Conducting comprehensive reviews of cryptographic protocols and implementation ensures that vulnerabilities are identified and addressed promptly.
2. Use of Strong Algorithms: Organizations should implement modern encryption standards such as AES (Advanced Encryption Standard) and RSA (Rivest-Shamir-Adleman) to secure sensitive data effectively. These algorithms are designed to withstand current attack methodologies.
3. Key Management Practices: Proper management of encryption keys is crucial. This includes generating strong keys, rotating them regularly, and securely storing them to prevent unauthorized access.
4. Employee Training: Regular training sessions can raise awareness among employees regarding the importance of cryptography and secure practices. This is pivotal, as human error can often lead to security breaches.
5. Adopting Multi-Factor Authentication (MFA): Implementing MFA adds an additional layer of security, making it more challenging for attackers to gain access to sensitive information, even if they manage to bypass encryption.
6. Staying Informed on Threats: Organizations should remain vigilant and informed about emerging threats and vulnerabilities in cryptographic practices. Engaging with cybersecurity communities can provide valuable insights and updates on best practices.
In summary, cryptography plays an indispensable role in safeguarding sensitive information within the realm of cybersecurity. By understanding the implications of cryptographic failures and actively enhancing their cryptographic measures, organizations can better protect themselves against the ever-evolving landscape of cyber threats.
The Role of Cryptography in Digital Signatures
In today’s digital age, the role of cryptography extends far beyond mere data protection; it forms the backbone of secure communications and transactions. One of its most significant applications is in digital signatures, which serve as a vital tool for ensuring authenticity, integrity, and non-repudiation in various online environments. Digital signatures not only facilitate trust in electronic transactions but also enhance the overall security of digital communications.
Digital signatures work through a combination of hashing and public-key cryptography. When a document is signed digitally, a hash of the document’s content is created using a cryptographic hash function. This hash is then encrypted with the signer’s private key, forming the digital signature. The recipient can verify this signature by decrypting it with the signer’s public key and comparing the resulting hash with their own computed hash of the received document. If both hashes match, it confirms that the document has not been altered and that it indeed comes from the purported signer. The significance of digital signatures in online transactions is immense, as they help prevent fraud and ensure that sensitive information is exchanged securely.
Legal Implications and Acceptance in Various Jurisdictions
The legal framework surrounding digital signatures varies significantly across jurisdictions, but many countries have adopted laws to recognize their validity. The Electronic Signatures in Global and National Commerce (ESIGN) Act in the United States, the eIDAS regulation in the European Union, and the Information Technology Act in India are examples of legislation that provide a legal basis for digital signatures. These laws usually stipulate that digital signatures carry the same weight as traditional handwritten signatures, provided they meet specific criteria.
This legal recognition is critical for industries that handle sensitive transactions, such as finance, healthcare, and real estate. For instance, banks often use digital signatures for loan agreements and mortgage documents to streamline processes while ensuring compliance with regulatory standards. In the healthcare sector, digital signatures facilitate secure patient consent forms, allowing for swift and trustworthy interactions between patients and providers.
Industries that Heavily Rely on Digital Signatures
Digital signatures are integral to various industries, enabling secure and efficient operations. Key sectors that heavily utilize this technology include:
- Finance: In banking, digital signatures are used for approving transactions and contracts, providing a secure method to verify users’ identities and ensure the integrity of financial data.
- Legal: Law firms utilize digital signatures for agreements, contracts, and filings to enhance efficiency and maintain the authenticity of legal documents.
- Healthcare: Medical institutions use digital signatures to manage patient records, consent forms, and prescriptions, ensuring compliance with regulations like HIPAA while improving operational efficiency.
- Government: Many government agencies have adopted digital signatures for official documents, tax filings, and permits, thereby reducing paperwork and expediting processes.
The adoption of digital signatures across these diverse sectors not only exemplifies their versatility but also underscores their essential role in maintaining security and trust in digital interactions.
The Future of Cryptography in Quantum Computing
The advent of quantum computing heralds a new era in technology that brings with it significant implications for the field of cryptography. Traditional cryptographic systems, which form the backbone of secure communications today, are facing unprecedented challenges posed by the rapidly evolving capabilities of quantum machines. As quantum computing becomes more mainstream, it is essential to understand both the threats it poses and the emerging countermeasures being developed to ensure data security in this new paradigm.
The potential challenges that quantum computing poses to current cryptographic systems are primarily rooted in its ability to perform complex calculations at speeds unimaginable with classical computers. Quantum algorithms, such as Shor’s algorithm, could efficiently factor large numbers, which is the foundation of many widely used encryption schemes, including RSA and ECC (Elliptic Curve Cryptography). This means that data encrypted with these conventional systems could potentially be decrypted in a matter of seconds or minutes, rendering current security measures ineffective. Furthermore, the principles of superposition and entanglement used in quantum computing open a realm where certain cryptographic techniques can be directly challenged, leading to vulnerabilities that were previously deemed secure.
Emerging Cryptographic Techniques Resistant to Quantum Attacks
In response to these looming threats, cryptographers are actively developing new techniques that are designed to withstand the power of quantum attacks. The field of post-quantum cryptography is burgeoning, focusing on algorithms that can resist quantum computational methods. Key emerging techniques include:
- Lattice-based Cryptography: This approach relies on mathematical structures known as lattices, which are believed to be difficult for quantum computers to solve. Lattice-based schemes, such as NTRU and Learning With Errors (LWE), offer both encryption and digital signature capabilities and are considered strong candidates for post-quantum security.
- Hash-based Cryptography: Utilizing the security of hash functions, hash-based signatures (like XMSS and SPHINCS+) provide a robust alternative by ensuring that any changes to the input data dramatically alter the output hash, making it impractical to forge signatures.
- Code-based Cryptography: This technique leverages error-correcting codes to create secure encryption systems. McEliece is a notable example that has remained secure against both classical and quantum attacks for decades.
These techniques utilize mathematical problems that are currently infeasible for quantum computers to solve effectively, thus paving the way for secure communication in a quantum future.
Comparing traditional cryptography with quantum cryptography reveals significant differences in terms of security and efficiency. Traditional cryptography, while effective today, is fundamentally vulnerable to the quantum threats mentioned earlier. In contrast, quantum cryptography, particularly Quantum Key Distribution (QKD), offers unparalleled security based on the principles of quantum mechanics. QKD allows two parties to generate a shared key that is provably secure, as any attempt at eavesdropping would disturb the quantum states being exchanged, alerting the parties involved.
However, implementing quantum cryptography can be resource-intensive and requires advanced technology, which may not be feasible for every application. While traditional cryptographic methods are generally faster for processing and require fewer resources, they lack the inherent security guarantees provided by quantum cryptography. Balancing efficiency and security remains an ongoing challenge as the field continues to evolve.
Overall, the future of cryptography in the context of quantum computing is both exciting and complex, demanding adaptive solutions to stay ahead of threats while ensuring the confidentiality and integrity of sensitive data.
Ethical Considerations Involving Cryptography
Cryptography stands at the intersection of privacy and security, presenting a myriad of ethical dilemmas. As technology evolves, the use of cryptography has become essential for protecting sensitive information. However, this power comes with significant responsibility, as the same technologies that guard personal data can also be exploited for malicious purposes.
The ethical landscape of cryptography is complex, particularly when evaluating the balance between individual privacy and national security. Governments often argue that they require access to encrypted communications to prevent terrorism and crime. This has led to calls for backdoors in encryption systems, potentially compromising user privacy. Users, on the other hand, advocate for strong encryption as a fundamental right against unwarranted surveillance. The tension between these opposing views raises critical questions about the extent to which privacy should be sacrificed for security.
Government Regulations and Their Impact on User Privacy
Government regulations play a pivotal role in shaping the use of cryptography. Various countries have implemented laws that aim to regulate encryption technology, often citing national security concerns. The consequences of such regulations can significantly impact user privacy in the following ways:
– Backdoor Legislation: Some governments propose laws requiring technology companies to build backdoors into encryption systems. This allows law enforcement access to encrypted data, but it inherently weakens overall security, making systems more vulnerable to hacking.
– Surveillance: Regulations can enable extensive government surveillance under the guise of security, infringing on civil liberties. This raises ethical concerns about the balance between protecting citizens and respecting their privacy.
– Compliance Burdens: Companies may face legal obligations that require them to compromise their encryption standards or disclose user data, affecting user trust and safety.
The implications of these regulations can result in a chilling effect on free speech and privacy, as people may self-censor if they fear their communications are being monitored.
Examples of Misuse of Cryptography and Consequences
While cryptography is a powerful tool for securing information, it can also be misused, leading to dire consequences. Here are notable examples:
– Ransomware Attacks: Cybercriminals use encryption to lock users out of their own data, demanding ransom payments to restore access. High-profile cases, such as the WannaCry ransomware attack, illustrate the devastating impact this can have on individuals and organizations alike.
– Dark Web Activities: Encryption facilitates illegal activities on the dark web, including drug trafficking and human trafficking. The anonymity provided by cryptographic techniques can shield criminal enterprises from law enforcement.
– State-Sponsored Cyber Warfare: Countries may use cryptographic methods to launch cyberattacks against rivals, stealing sensitive information or disrupting critical infrastructure. Such actions can escalate international tensions and undermine trust between nations.
Ultimately, the ethical considerations in the realm of cryptography require a nuanced approach that respects both privacy rights and security needs. In navigating this landscape, it is crucial to strike a balance that fosters trust and safety in an increasingly digital world.
The Interplay Between Cryptography and Blockchain Technology
Cryptography is the backbone of blockchain technology, ensuring secure communication and integrity of data within decentralized networks. By utilizing cryptographic principles, blockchain systems maintain trust and transparency, making them an essential component in the digital economy. As blockchain continues to evolve, the reliance on cryptographic methods deepens, paving the way for innovative applications across various industries.
The fundamental role of cryptography in ensuring the integrity of blockchain systems revolves around creating secure and immutable records. Each block in a blockchain contains a unique cryptographic hash of the previous block, which links them in a chain. This ensures that any alteration to a block would require recalculating all subsequent blocks, making tampering nearly impossible. For instance, Bitcoin employs the SHA-256 hashing algorithm to secure its transactions. When a transaction is initiated, it is hashed, and that hash is unique to the transaction data. If even a single detail of the transaction changes, the hash will change, alerting the network to potential fraud.
Consensus Algorithms and Cryptographic Principles
Consensus algorithms are critical in maintaining the security and integrity of blockchain networks. These algorithms are designed to achieve agreement among distributed nodes in the network, ensuring that they reach a consensus on the validity of transactions. Various consensus mechanisms leverage cryptographic techniques to enhance this security.
One of the most widely known consensus algorithms is Proof of Work (PoW), utilized by Bitcoin. PoW requires miners to solve complex mathematical problems, which involve significant computational power and energy. The cryptographic puzzles ensure that only those who contribute computational work can validate transactions, thus securing the network against attacks.
Another widely used consensus mechanism is Proof of Stake (PoS). In PoS, validators are chosen based on the number of coins they hold and are willing to “stake” as collateral. Cryptography plays a pivotal role in this method by ensuring that validators cannot easily manipulate the system without risking their assets. Moreover, it significantly reduces the energy consumption associated with mining.
Challenges and Advantages of Cryptography in Blockchain Applications
The implementation of cryptography in blockchain technology brings a range of challenges and advantages. One major challenge is scalability. As the number of users and transactions increases, the cryptographic processes can lead to slower transaction times and higher fees. Additionally, the complexity of these cryptographic techniques can pose difficulties in terms of user understanding and accessibility.
On the other hand, the advantages are substantial. Cryptography provides enhanced security against fraud and cyber-attacks, fostering trust among users. The immutability of blockchain records, supported by cryptographic hashing, ensures that once data is recorded, it cannot be altered or deleted. This characteristic is particularly beneficial in sectors like finance and supply chain management, where transparency and accountability are paramount.
In summary, cryptography serves as a crucial element in the architecture of blockchain technology, influencing its security, transaction verification, and overall integrity. The interplay between these two domains continues to shape the future of secure digital transactions and decentralized systems.
Last Point
In summary, the evolution of cryptography is not just a tale of technological advances but also a reflection of humanity’s ongoing quest for security and privacy. As we face emerging challenges, particularly with advancements like quantum computing, the continued development of cryptographic techniques will be crucial. Our understanding of cryptography empowers us to navigate the complexities of cybersecurity and digital interactions, ensuring that our communications remain secure in an ever-evolving digital world.
Q&A
What is the primary purpose of cryptography?
The primary purpose of cryptography is to secure information by transforming it into a format that is unreadable to unauthorized users, ensuring confidentiality, integrity, and authenticity.
What are symmetric and asymmetric encryption?
Symmetric encryption uses the same key for both encryption and decryption, while asymmetric encryption uses a pair of keys, one public and one private, for secure communication.
How does hashing differ from encryption?
Hashing transforms data into a fixed-size string of characters, which is unique to the original data, while encryption transforms data into an unreadable format that can be reverted back to its original form using a key.
Can cryptography guarantee complete security?
No, while cryptography significantly enhances security, it cannot provide absolute guarantees, as vulnerabilities may arise from implementation flaws or user errors.
What role does cryptography play in everyday applications?
Cryptography secures various everyday applications, including online banking, e-commerce transactions, email communications, and data storage, thereby protecting sensitive information from unauthorized access.