Vulnerability Assessment plays a crucial role in today’s cybersecurity landscape, serving as the foundation for understanding and managing potential risks within various systems and networks. With the rapid evolution of technology and increasing cyber threats, it’s essential for organizations to comprehensively identify and address vulnerabilities that could lead to significant security breaches.
By systematically evaluating their infrastructures, businesses can uncover weaknesses, prioritize remediation efforts, and safeguard sensitive information. Understanding the basic concepts and definitions surrounding vulnerability assessments empowers organizations to navigate the complexities of cybersecurity effectively.
Understanding the Fundamentals of Vulnerability Assessments
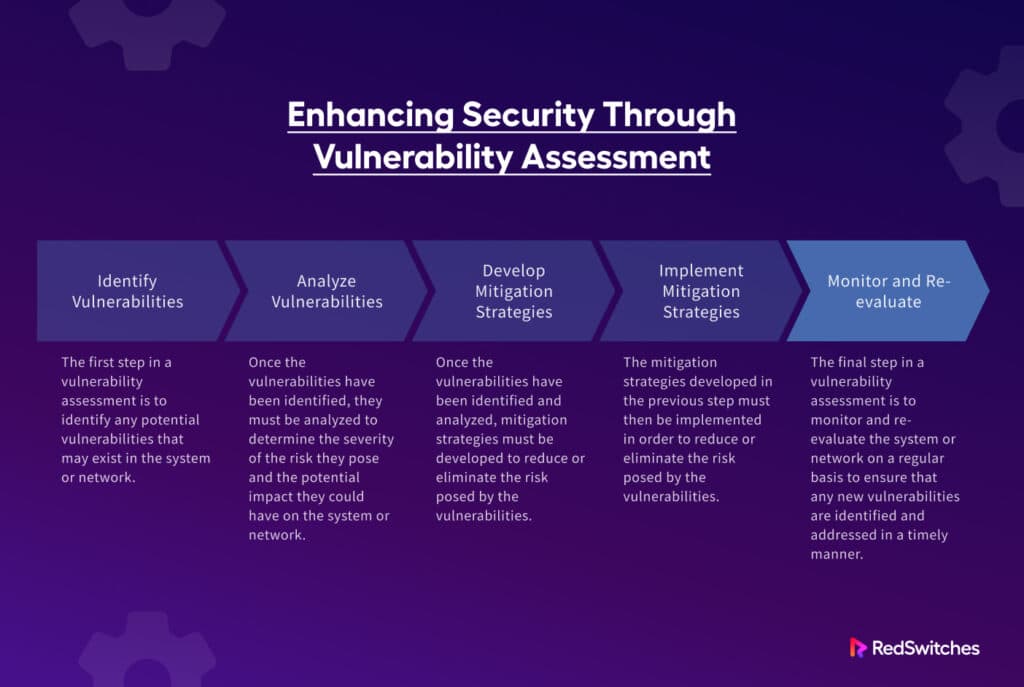
Vulnerability assessments are a critical component of any organization’s security framework, aimed at identifying weaknesses in systems, applications, and networks. By systematically evaluating these components, organizations can better understand their security posture and take appropriate measures to mitigate risks. This process helps in safeguarding sensitive information and maintaining the integrity of systems against potential threats.
The basic concept of a vulnerability assessment involves a thorough examination of an organization’s infrastructure to pinpoint vulnerabilities that could be exploited by attackers. Vulnerabilities may arise from configuration errors, software bugs, or even inadequate security policies. Identifying these weaknesses allows organizations to prioritize their remediation efforts based on the risk associated with each vulnerability.
Significance of Identifying Vulnerabilities
Recognizing vulnerabilities is essential for protecting an organization’s assets and information. It provides insights into potential attack vectors, enabling proactive measures to be taken before an incident occurs. The significance of identifying vulnerabilities spans various systems and networks, ensuring that both internal and external threats are addressed.
For instance, organizations may encounter common vulnerabilities such as:
- Unpatched Software: Software that has not been updated can harbor known vulnerabilities that hackers can exploit.
- Weak Passwords: Utilizing easily guessable or default passwords can provide unauthorized access to sensitive data.
- Misconfigured Systems: Incorrectly configured firewalls or servers can inadvertently expose critical assets to the internet.
- Sensitive Data Exposure: Inadequate encryption can lead to the exposure of personal and financial information, presenting significant risks to both organizations and individuals.
“Identifying vulnerabilities is not just about finding flaws; it’s about understanding the landscape of risks that organizations face in their digital environments.”
Employing vulnerability assessments helps organizations not only to comply with regulatory requirements but also to foster trust with clients and customers. By demonstrating a commitment to security, organizations can enhance their reputation and build stronger relationships in a competitive marketplace.
The Methodologies Used in Conducting Vulnerability Assessments

Vulnerability assessments are vital in identifying weaknesses that could be exploited in an organization’s security infrastructure. Different methodologies come into play when conducting these assessments, each with unique approaches that help organizations understand their risk landscape.
One of the primary distinctions in vulnerability assessment methodologies is between qualitative and quantitative assessment methods. Qualitative assessments focus on descriptive analysis, emphasizing the characteristics and contexts of vulnerabilities, which allows for a broader understanding of potential risks without relying heavily on numerical data. In contrast, quantitative assessments employ numerical values, enabling organizations to calculate risk with greater precision, often producing metrics that can drive decision-making.
Comparison of Qualitative and Quantitative Assessment Methods
Qualitative methodologies typically involve expert opinions, interviews, and surveys to gather data on vulnerabilities. They are particularly effective in environments where subjective judgments about risk are necessary. This method allows for the consideration of less tangible factors, such as organizational culture and environmental variables. However, qualitative assessments can sometimes lack the rigor of quantitative methods, as they may be influenced by personal biases.
On the other hand, quantitative methodologies apply statistical techniques and frameworks to evaluate vulnerabilities. This approach usually involves the use of scoring systems that provide measurable risk levels. While quantitative assessments can yield precise and defensible data, they may overlook the nuances of certain vulnerabilities that do not lend themselves easily to numerical representation.
It’s important to consider that both methods have their merits and can often complement each other. A blended approach can provide a well-rounded view of the vulnerability landscape, ensuring that both measurable risks and contextual factors are taken into account.
Several frameworks are widely recognized and utilized in the field of vulnerability assessments, each providing structured methodologies to improve the accuracy and effectiveness of assessments. These frameworks help organizations standardize their approach and ensure that all relevant factors are considered during the assessment process. Below is a list of popular frameworks used in vulnerability assessments:
- Common Vulnerability Scoring System (CVSS): A standardized method for assessing the severity of vulnerabilities, providing a numerical score that reflects the potential impact of a threat.
- NIST Cybersecurity Framework: A comprehensive framework that provides guidelines for managing cybersecurity risks, incorporating assessment methodologies to identify vulnerabilities and improve security posture.
- OWASP Top Ten: A list of the ten most critical web application security risks, providing a framework for assessing and mitigating vulnerabilities in web applications.
- ISO/IEC 27001: An international standard outlining the requirements for establishing, implementing, maintaining, and continuously improving an information security management system (ISMS).
- FAIR (Factor Analysis of Information Risk): A framework that focuses on quantifying risk in financial terms, enabling organizations to prioritize vulnerabilities based on potential financial impact.
These frameworks not only guide the assessment process but also help organizations communicate risks effectively to stakeholders, ensuring a comprehensive understanding of their security posture.
Tools and Technologies for Effective Vulnerability Assessments
Vulnerability assessments are critical in identifying security weaknesses within systems, applications, and networks. Utilizing the right tools can significantly enhance the effectiveness of these assessments, enabling organizations to proactively manage their security posture. There is a wide array of tools available, each designed to serve specific needs and scenarios in vulnerability scanning and assessment.
Popular Vulnerability Assessment Tools
Several tools have emerged as leaders in the vulnerability assessment domain, each offering unique features and capabilities. Below, we delve into some of the most popular tools, providing insights into their functionalities.
Nessus is widely recognized for its comprehensive scanning capabilities, allowing users to identify vulnerabilities across various platforms. It supports compliance checks and includes a robust plugin architecture, which enables users to customize and extend its functionality. Nessus is particularly known for its user-friendly interface and detailed reporting features, which provide actionable insights.
Qualys has gained traction due to its cloud-based infrastructure, allowing for seamless integration and scalability. This tool offers a suite of security solutions, including vulnerability management, web application scanning, and continuous monitoring. Qualys is notable for its real-time visibility and extensive database of vulnerabilities, enabling organizations to stay ahead of potential threats.
OpenVAS, an open-source alternative, provides a powerful framework for vulnerability scanning. It is highly configurable and offers a variety of scanning options, including network and web application scans. OpenVAS is appreciated for its cost-effectiveness and community support, making it a popular choice among smaller organizations and security enthusiasts.
The following table compares key features of Nessus, Qualys, and OpenVAS across several categories:
| Feature | Nessus | Qualys | OpenVAS |
|---|---|---|---|
| Deployment Model | On-premises or Cloud | Cloud-based | Open-source |
| Compliance Scanning | Yes | Yes | No |
| Customizable Plugins | Yes | No | Yes |
| Reporting Features | Advanced | Comprehensive | Basic |
| User Interface | User-friendly | User-friendly | Less intuitive |
| Integration Options | APIs available | Extensive | Limited |
These tools play a pivotal role in automating the vulnerability assessment process, making it easier for organizations to identify and remediate vulnerabilities. By leveraging these tools, businesses can enhance their security posture and reduce the risks associated with potential cyber threats. Investing in the right vulnerability assessment tools is essential for maintaining a proactive security strategy.
The Role of Vulnerability Management in Cybersecurity Strategy
Vulnerability management is a critical component of an organization’s cybersecurity strategy that encompasses the identification, evaluation, treatment, and reporting of security weaknesses. This process is not just a technical necessity but a strategic imperative that allows organizations to maintain a proactive posture against ever-evolving cyber threats. By effectively managing vulnerabilities, organizations can significantly reduce their attack surface and enhance their overall security posture.
The integration of vulnerability management into an organization’s cybersecurity framework ensures that potential security gaps are systematically identified and addressed. This continual process aligns with the broader objectives of risk management, compliance, and incident response. Effective vulnerability management contributes to a holistic cybersecurity strategy by enabling organizations to prioritize risks, allocate resources appropriately, and make informed decisions regarding their security investments.
Lifecycle of Vulnerability Management
Understanding the lifecycle of vulnerability management is essential for organizations aiming to strengthen their cybersecurity defenses. This lifecycle generally encompasses several key stages, each crucial for effective vulnerability management:
1. Identification: The first step involves scanning systems and networks to identify vulnerabilities. Tools such as vulnerability scanners and penetration testing software are commonly used to detect security flaws or weaknesses in software, hardware, and configurations. Regular scan schedules should be established to ensure ongoing assessment.
2. Assessment: After identifying vulnerabilities, the next phase is to assess their severity and potential impact. This involves analyzing the likelihood of exploitation and the potential damage that could result from a successful attack. The Common Vulnerability Scoring System (CVSS) is often employed to assign a score to vulnerabilities, helping prioritize them based on risk.
3. Prioritization: Not all vulnerabilities pose the same level of risk, making prioritization essential. By categorizing vulnerabilities based on factors such as exploitability, potential impact, and the criticality of the affected system, organizations can focus their efforts on addressing the most significant threats first.
4. Remediation: This step involves implementing measures to fix identified vulnerabilities. Remediation strategies may include applying patches, reconfiguring systems, or introducing additional security controls. Timely remediation is vital to mitigate risks and protect organizational assets.
5. Reporting and Monitoring: Post-remediation, organizations should report on the status of vulnerabilities and track progress over time. Continuous monitoring ensures that newly identified vulnerabilities are addressed promptly and that the security environment remains robust.
6. Review and Improvement: Finally, organizations should periodically review their vulnerability management processes and outcomes. This includes evaluations of the effectiveness of remediation efforts and updates to scanning tools and techniques as new threats emerge.
This structured approach to vulnerability management ensures a comprehensive strategy, enabling organizations to remain resilient against cyber threats.
Challenges and Limitations in Vulnerability Assessments
Vulnerability assessments are crucial for identifying and mitigating potential security threats within an organization. However, the process is fraught with challenges and limitations that can hinder its effectiveness. Understanding these hurdles is essential for organizations seeking to strengthen their security posture.
One of the primary challenges during vulnerability assessments is the complexity and ever-evolving nature of technological environments. Organizations often employ a mix of legacy systems and modern applications, creating a patchwork that can be difficult to analyze comprehensively. This complexity can lead to incomplete assessments if certain systems are overlooked or misconfigured. Additionally, the rapid pace of software updates and new vulnerabilities emerging daily complicates the ability to maintain up-to-date assessments.
Another significant issue is the prevalence of false positives and false negatives. False positives occur when a vulnerability scanner flags a benign issue as a risk, potentially leading security teams to waste time and resources on non-existent problems. Conversely, false negatives can be even more dangerous, as they represent actual vulnerabilities that go undetected, leaving organizations exposed to attacks. The accuracy of vulnerability assessment tools directly impacts the reliability of the findings, making it critical to choose the right tools and configurations.
Resource constraints are another notable limitation in conducting thorough vulnerability assessments. Many organizations operate with limited budgets and personnel, often resulting in a lack of dedicated security staff or insufficient training for existing employees. This scarcity can lead to rushed assessments or reliance on automated tools that may not capture the full scope of vulnerabilities present in the network.
To effectively mitigate these challenges, organizations can adopt best practices that enhance the vulnerability assessment process. These practices include:
- Regularly update and configure vulnerability assessment tools to ensure they are effective against the latest threats.
- Conduct periodic training for security personnel to keep them informed about the latest vulnerabilities and assessment techniques.
- Implement a multi-layered approach that combines automated scans with manual testing for a more comprehensive view of vulnerabilities.
- Establish clear protocols for prioritizing vulnerabilities to ensure that critical issues are addressed promptly.
- Engage third-party security experts for independent assessments to gain an outside perspective on vulnerabilities.
By applying these best practices, organizations can better navigate the challenges and limitations inherent in vulnerability assessments, thus bolstering their security defenses against potential threats.
The Future of Vulnerability Assessments in an Evolving Threat Landscape
As organizations continue to digitize operations and adopt new technologies, vulnerability assessments are becoming increasingly critical. The future of vulnerability assessments is poised to evolve significantly as emerging technologies reshape the landscape. This shift is driven by the need for organizations to protect themselves against increasingly sophisticated cyber threats, making vulnerability assessments more essential than ever before.
Emerging technologies, particularly artificial intelligence (AI) and machine learning (ML), are revolutionizing how vulnerabilities are identified and managed. Traditional vulnerability assessment methods often rely on manual processes, making it challenging to keep pace with the rapid advancement of threats. AI and ML can analyze vast amounts of data quickly and accurately, detecting patterns and anomalies that may indicate a vulnerability. By leveraging these technologies, organizations can automate and streamline their vulnerability assessment processes, making them more efficient and effective.
Impact of Artificial Intelligence and Machine Learning on Identifying Vulnerabilities
The integration of AI and ML into vulnerability assessments is transforming the way organizations approach security. These technologies enhance the ability to identify vulnerabilities through several mechanisms:
– Automated Scanning: AI-driven tools can conduct continuous and automated scans of systems and networks, identifying potential vulnerabilities in real time. This proactive approach minimizes the window of exposure to threats.
– Predictive Analytics: Machine learning algorithms can analyze historical data to predict where vulnerabilities are likely to appear based on trends and past incidents. This allows organizations to prioritize their assessments and focus on areas of higher risk.
– Anomaly Detection: AI can identify unusual patterns of behavior that might indicate a security breach or vulnerability. By flagging these anomalies, organizations can respond swiftly to potential threats.
– Risk Assessment: AI systems can assess the severity and potential impact of identified vulnerabilities, helping organizations allocate resources more effectively to address the most critical issues.
The adoption of these technologies offers organizations significant advantages in their vulnerability management strategies. For example, a multinational corporation recently implemented an AI-driven vulnerability scanning solution that reduced their time to identify and remediate vulnerabilities from weeks to hours. This rapid response capability significantly bolstered their security posture and reduced the risk of data breaches.
Looking ahead, the vulnerability assessment process is expected to evolve dramatically over the next decade. The following trends are predicted to shape the future of vulnerability assessments:
– Increased Automation: As AI and ML technologies continue to advance, the automation of vulnerability assessments will become more prevalent. Organizations will rely less on manual processes and more on automated systems that provide continuous monitoring and assessment.
– Integration with Threat Intelligence: Future vulnerability assessments will likely incorporate real-time threat intelligence, allowing organizations to prioritize vulnerabilities based on current threat landscapes and emerging attack vectors.
– Enhanced Collaboration: The future may see greater collaboration between security teams and development teams, with vulnerability assessments becoming an integral part of the DevOps cycle. This integration will help to identify and remediate vulnerabilities early in the development process.
– Focus on Cloud Security: As more businesses migrate to cloud environments, vulnerability assessments will need to adapt to address the unique security challenges posed by cloud infrastructures, including misconfigurations and shared responsibilities.
– Regulatory Compliance: As regulations around data privacy and security evolve, organizations will increasingly incorporate compliance requirements into their vulnerability assessment processes, ensuring that they meet industry standards while protecting sensitive information.
By understanding these trends and leveraging advanced technologies, organizations can better prepare for the future of vulnerability assessments, ensuring robust protection against evolving cyber threats.
Outcome Summary
In conclusion, Vulnerability Assessment is not just a technical exercise but a vital component of a robust cybersecurity strategy. As organizations continue to face an ever-changing threat landscape, the insights gained from thorough assessments will enable them to proactively address vulnerabilities and enhance their overall security posture. The future of vulnerability assessments promises to be dynamic, driven by advancements in technology and the need for continuous improvement in protecting digital assets.
User Queries
What is a Vulnerability Assessment?
A Vulnerability Assessment is a systematic evaluation of a system or network to identify and prioritize vulnerabilities that could be exploited by attackers.
How often should Vulnerability Assessments be conducted?
It’s recommended to conduct Vulnerability Assessments at least quarterly or after significant changes to the IT environment.
Are Vulnerability Assessments the same as Penetration Testing?
No, Vulnerability Assessments identify potential vulnerabilities, while Penetration Testing simulates attacks to exploit those vulnerabilities.
What tools are commonly used for Vulnerability Assessments?
Common tools include Nessus, Qualys, and OpenVAS, each offering unique features for scanning and reporting vulnerabilities.
Can Vulnerability Assessments identify all security weaknesses?
No, while they are comprehensive, some weaknesses may go undetected due to limitations like false positives and the evolving nature of threats.
What are common challenges faced during Vulnerability Assessments?
Challenges include resource constraints, managing false positives/negatives, and keeping up with rapidly changing technologies.