Firewall technology serves as a crucial guardian in the realm of network security, standing firm against a myriad of cyber threats that can compromise sensitive data and system integrity. By acting as a barrier between trusted internal networks and untrusted external ones, firewalls play an essential role in protecting organizations from malicious attacks and unauthorized access. With various types of firewalls available, including hardware and software solutions, each brings unique functionalities and advantages to the table, ensuring tailored protection based on specific needs.
The evolution of firewall technology over the years showcases its adaptability in response to the ever-changing cybersecurity landscape, highlighting advancements that have significantly enhanced their effectiveness. From the fundamental principles of packet filtering to the sophisticated stateful inspection, understanding these concepts is key to grasping how modern firewalls operate. As we delve deeper into this topic, we will explore the vital role firewalls play within corporate environments, best practices for configuration, common misconceptions, and the exciting future trends shaping this technology.
Understanding the Fundamental Principles of Firewalls
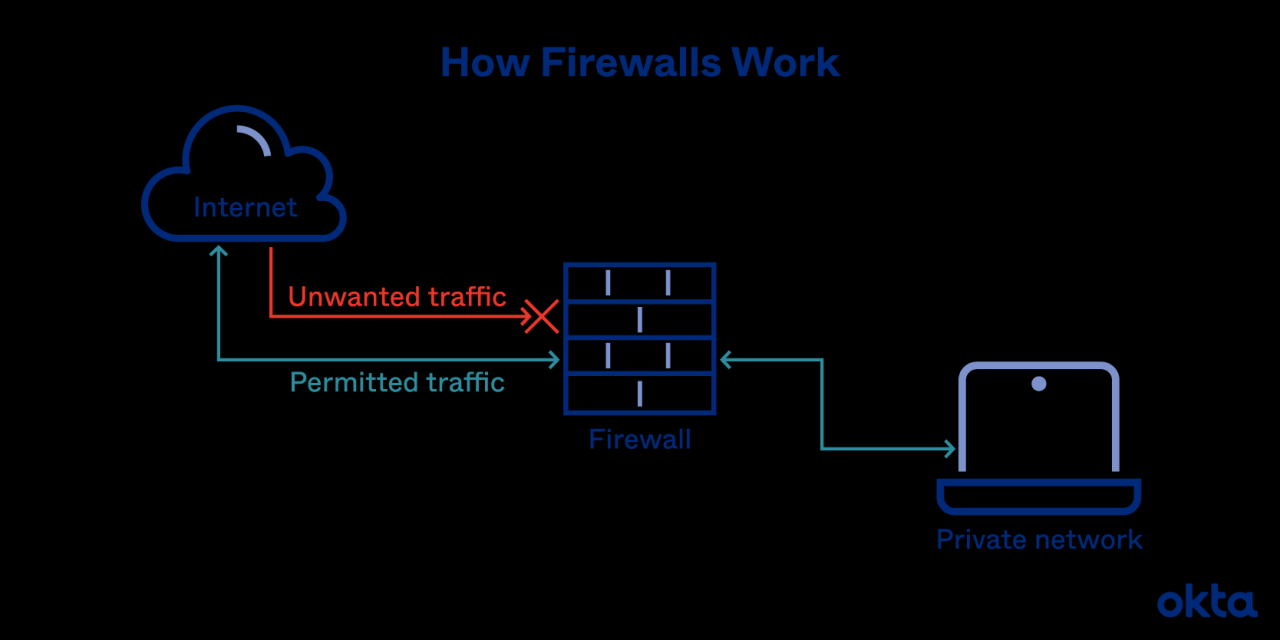
Firewalls serve as critical components in the landscape of network security, acting as gatekeepers that monitor and control incoming and outgoing network traffic. They are essential for protecting sensitive data and maintaining the integrity of computer networks from unauthorized access and cyber threats. By establishing a barrier between trusted internal networks and untrusted external environments, firewalls help mitigate various security risks.
The basic concept of a firewall revolves around its ability to filter traffic based on predetermined security rules. Firewalls can be implemented in both hardware and software forms, providing flexibility depending on the specific security requirements of an organization. The functionality of a firewall is primarily determined by its type—each designed to handle specific scenarios and offer distinct levels of security.
Types of Firewalls and Their Functionalities
Understanding the different types of firewalls and their respective functionalities is crucial for effective network security management. Each firewall type provides unique features that cater to various security needs:
- Packet-Filtering Firewalls: These are the most basic form of firewalls. They inspect packets of data against a set of filter rules and allow or deny them based on their source, destination, and port numbers. Packet-filtering firewalls operate at the network layer and do not maintain state information.
- Stateful Inspection Firewalls: More advanced than packet-filtering firewalls, stateful inspection firewalls track the state of active connections and make decisions based on the context of the traffic. They analyze packets and maintain a state table to provide enhanced security.
- Proxy Firewalls: Acting as intermediaries between users and the internet, proxy firewalls intercept all traffic to and from the network. They can provide additional features such as content filtering and caching to improve performance and security.
- Next-Generation Firewalls (NGFW): These firewalls combine traditional firewall features with advanced security functionalities like intrusion detection and prevention systems (IDPS), application awareness, and integrated threat intelligence. They offer a comprehensive solution for modern security challenges.
Key terms associated with firewalls include “packet filtering,” which refers to the process of inspecting data packets, and “stateful inspection,” which involves tracking the state of connections to make intelligent filtering decisions. Understanding these key concepts is vital for implementing robust firewall solutions that effectively safeguard network infrastructures.
The Evolution of Firewall Technology Over the Years
The development of firewall technology has been a critical component in the ongoing battle against cybersecurity threats. From their inception to their current state, firewalls have undergone significant transformations, adapting to the changing landscape of digital threats and technology. Understanding this evolution reveals the challenges and advancements that have shaped modern cybersecurity practices.
The early days of firewalls can be traced back to the late 1980s, when organizations began to realize the importance of protecting their networks from unauthorized access. The first firewalls were primarily packet-filtering systems that analyzed the headers of data packets to determine whether to allow or block traffic based on predetermined rules. These rudimentary systems laid the foundation for what would become a complex and essential component of network security.
Advancements in Firewall Capabilities
As technology progressed, firewalls evolved from basic packet filters to more sophisticated solutions. The introduction of stateful inspection firewalls in the 1990s marked a significant leap forward. Unlike their predecessors, these systems kept track of active connections and made decisions based on the context of the traffic rather than just static rules. This advancement increased the effectiveness of firewalls in thwarting more complex attacks.
The evolution didn’t stop there; the emergence of application-layer firewalls allowed for deeper inspection of traffic at the application level. These firewalls could analyze data packets and make decisions based on the specific application protocols being used. This capability enabled organizations to protect against application-layer attacks, which had become more prevalent with the rise of web-based applications.
The introduction of next-generation firewalls (NGFW) brought a multitude of advanced features, including intrusion prevention systems (IPS), deep packet inspection (DPI), and user identity awareness. These capabilities significantly enhanced the ability to detect and mitigate threats in real-time. NGFWs are designed to understand the context of traffic, providing a more comprehensive security solution that integrates seamlessly with other security technologies.
Comparison of Early and Contemporary Firewalls
The advancements in firewall technology can be starkly contrasted between early firewalls and modern solutions. Early firewalls, primarily packet filters, had limited effectiveness against sophisticated attacks. Their complexity was minimal, focusing mainly on basic rules without context.
In contrast, contemporary firewalls are characterized by their multifaceted approach to security. They not only filter traffic but also incorporate machine learning and artificial intelligence to adapt to new threats dynamically. This modern complexity allows for a layered security strategy, enabling organizations to respond swiftly to new attack vectors.
“Modern firewalls are not just defensive tools; they are proactive systems designed to anticipate and mitigate threats before they can exploit vulnerabilities.”
The shift from simple to sophisticated firewall solutions has had a significant impact on organizations’ cybersecurity strategies. As threats have evolved, so too has the technology designed to combat them, underscoring the vital role firewalls play in protecting sensitive data and maintaining network integrity.
The Role of Firewalls in Corporate Network Security
Implementing firewalls in a corporate environment is of paramount significance. Firewalls serve as a first line of defense in network security, acting as barriers between trusted internal networks and untrusted external ones. By regulating incoming and outgoing network traffic based on predetermined security rules, firewalls protect sensitive corporate data from unauthorized access and attacks.
Firewalls are designed to mitigate a variety of common threats that businesses face. These include malware attacks, unauthorized access attempts, and data breaches. Companies often encounter threats like phishing attacks, where attackers impersonate legitimate entities to steal sensitive information. Additionally, Distributed Denial-of-Service (DDoS) attacks pose significant risks by overwhelming networks with traffic, thereby disrupting services. Firewalls play a crucial role in blocking these threats by analyzing and filtering traffic before it reaches critical systems.
Integration of Firewalls with Other Security Measures
The effectiveness of firewalls is greatly enhanced when integrated with other security measures, forming a multi-layered defense strategy. This comprehensive approach ensures that businesses are better protected against a variety of cyber threats. The integration of firewalls with additional security solutions can address vulnerabilities more effectively and provide a more robust security posture.
Key components that can complement firewalls include:
- Intrusion Detection Systems (IDS): These systems monitor network traffic for suspicious activity and can alert administrators to potential threats that firewalls might not detect.
- Virtual Private Networks (VPNs): VPNs secure remote connections to the corporate network, ensuring that data transmitted over the internet is encrypted and protected from eavesdroppers.
- Endpoint Protection Solutions: These tools safeguard individual devices connected to the network, preventing malware and other threats from reaching critical systems.
- Security Information and Event Management (SIEM): SIEM systems aggregate and analyze security data in real-time, helping to identify and respond to incidents quickly.
By combining these security elements, organizations create a layered defense that not only leverages the capabilities of firewalls but also addresses potential gaps. This holistic approach allows for proactive monitoring and response, increasing overall resilience against cyber threats.
“A well-configured firewall is a critical asset in safeguarding corporate networks against evolving cyber threats.”
Configuration Best Practices for Firewalls
Configuring firewalls effectively is crucial for maintaining the security and performance of networks. By following best practices, organizations can significantly reduce vulnerabilities and ensure that their firewall operates optimally. This section explores essential steps, established protocols, and a checklist of common configuration mistakes to avoid during firewall setup.
Essential Steps in Configuring Firewalls
To achieve optimal performance and security, several key steps should be followed when configuring firewalls. These steps lay the groundwork for a robust firewall setup that can withstand various cyber threats.
- Define Security Policies: Establish clear security policies that dictate acceptable use, data protection, and access controls.
- Implement Network Segmentation: Divide your network into segments to reduce the attack surface and increase control over traffic between different zones.
- Regularly Update Firewall Rules: Continuously review and update firewall rules to adapt to changing security needs and threats.
- Enable Logging and Monitoring: Activate logging features to monitor traffic and events, which aids in identifying and responding to potential security incidents.
- Test the Configuration: Conduct regular penetration testing and vulnerability assessments to verify that the firewall configuration is effective against threats.
Established Protocols During Initial Setup
During the initial setup of a firewall, certain protocols should be firmly established to ensure proper functionality and security. These protocols help in maintaining consistency and adherence to security best practices.
- Use Strong Authentication: Implement multi-factor authentication for access to the firewall management interface.
- Change Default Credentials: Replace default usernames and passwords with strong, unique credentials to prevent unauthorized access.
- Configure Timeouts: Set session timeout limits to reduce the risk of unauthorized access through idle sessions.
- Establish a Backup Strategy: Regularly back up the firewall configuration to avoid data loss and allow for quick recovery in case of a failure.
Common Configuration Mistakes to Avoid
It’s important to be aware of common configuration mistakes that can lead to security vulnerabilities or operational issues. By avoiding these pitfalls, organizations can enhance their firewall effectiveness.
“A well-configured firewall is a critical line of defense against cyber threats.”
- Neglecting to Document Changes: Failing to document configuration changes can lead to confusion and difficulty in troubleshooting.
- Overly Permissive Rules: Creating rules that allow excessive access can expose the network to unnecessary risks.
- Ignoring Unused Services: Failing to disable unnecessary services and ports can create additional vulnerabilities.
- Not Regularly Reviewing Rules: Static rules that are never reviewed can become outdated and ineffective in addressing current threats.
- Inadequate Testing Before Deployment: Skipping testing can result in unforeseen issues once the firewall is live.
The Distinction Between Hardware and Software Firewalls
In the realm of network security, firewalls serve as essential barriers against unauthorized access and threats. Understanding the distinction between hardware and software firewalls is crucial for implementing effective security measures tailored to specific environments. Each type of firewall offers unique benefits and drawbacks, making them suitable for different deployment scenarios.
Deployment Scenarios for Hardware and Software Firewalls
When selecting a firewall, it’s important to consider the deployment scenarios suited for hardware and software solutions. Hardware firewalls are typically employed at the network perimeter, acting as a gatekeeper between the internal network and external threats. They are ideal for larger organizations with multiple users and devices needing centralized security management.
Software firewalls, on the other hand, can be installed on individual devices, providing localized protection. They are commonly used in home networks or small businesses where cost-effectiveness and user-specific customization are priorities. Each option fits distinct environments:
- Hardware Firewalls: Best suited for enterprise-level organizations that manage vast networks with high traffic volumes. They offer robust protection and can handle multiple connections without degrading performance.
- Software Firewalls: Ideal for personal computers or smaller setups where individual user preferences and specific application controls are necessary. They provide flexibility and ease of installation for those without extensive IT resources.
Advantages and Disadvantages of Hardware Firewalls
Evaluating the advantages and disadvantages of hardware firewalls can help organizations decide if they meet their security needs.
- Advantages:
- Offers comprehensive security for all devices on the network.
- Typically faster than software firewalls due to dedicated processing power.
- Requires minimal configuration on individual devices.
- Disadvantages:
- Higher initial investment and ongoing maintenance costs.
- Less flexibility in configuring user-specific settings.
- Physical presence required, limiting deployment options in remote locations.
Advantages and Disadvantages of Software Firewalls
Software firewalls also present their own set of advantages and disadvantages, making them suitable for different scenarios.
- Advantages:
- Cost-effective and accessible for small businesses and home users.
- Highly configurable, allowing users to set specific rules for applications.
- Easy to update and personalize based on individual security needs.
- Disadvantages:
- Can slow down device performance when multiple rules are enforced.
- Requires individual setup on each device, which may be impractical for larger networks.
- Potential vulnerability if not regularly updated or configured correctly.
Ideal Environments for Each Firewall Solution
Different environments benefit from either hardware or software firewalls based on their specific needs.
- Hardware Firewalls: Recommended for corporate environments where multiple users access the network simultaneously. They provide a strong first line of defense against external threats and can be integrated with other security measures to fortify overall protection.
- Software Firewalls: Best for personal computers, remote work setups, or small offices where individual user preferences and application-specific rules are necessary. They offer a tailored approach to security that adapts to the user’s unique requirements.
Assessing the Performance of Firewall Solutions
Evaluating the performance of firewall solutions is crucial for ensuring the security of network environments. Various metrics and testing methods are employed to gauge how effectively a firewall can protect against threats and manage network traffic.
One essential aspect of assessing firewall performance is the identification of key metrics that provide insights into their effectiveness. These metrics can include throughput, latency, connection handling capacity, and the rate of false positives and negatives. Throughput refers to the amount of data the firewall can process within a specific timeframe, while latency measures the delay introduced by the firewall. Connection handling capacity indicates the number of concurrent connections a firewall can manage, and false positive/negative rates assess how accurately the firewall identifies threats versus benign traffic.
Key Metrics for Evaluating Firewall Performance
Understanding the metrics used to evaluate firewall performance helps organizations make informed decisions. The following key metrics are frequently considered:
- Throughput: The volume of data processed by the firewall, generally measured in Mbps or Gbps. Higher throughput indicates better performance.
- Latency: The time delay incurred when traffic passes through the firewall. Minimal latency is desired to maintain network performance.
- Connection Handling Capacity: The maximum number of simultaneous connections that can be processed without performance degradation.
- False Positive Rate: The frequency with which legitimate traffic is incorrectly identified as a threat.
- False Negative Rate: The rate at which actual threats are not detected by the firewall.
Evaluating these metrics provides a comprehensive overview of a firewall’s capabilities and helps identify potential weaknesses.
Methods for Testing Firewall Efficiency
Testing the efficiency of firewall solutions involves several methodologies to ensure they effectively block potential threats. Common testing methods include:
- PEN Testing: Conducting penetration tests simulates cyber-attacks to evaluate how well the firewall can withstand real-world threats.
- Traffic Simulation: Generating controlled traffic, both legitimate and malicious, to assess how the firewall responds under various conditions.
- Performance Benchmarking: Comparing the firewall’s performance against industry standards or competing products to gauge its relative effectiveness.
- Log Analysis: Reviewing firewall logs for insights into its detection and blocking capabilities, including identifying patterns in false positives and negatives.
These methods are integral in ensuring that a firewall not only performs well under stress but also effectively mitigates risk from various cyber threats.
Comparison of Popular Firewall Products
To facilitate decision-making, a comparison table of popular firewall products based on performance metrics is provided below. This table highlights the performance ratings of various solutions, enabling users to quickly identify which product may best meet their needs.
| Firewall Product | Throughput (Mbps) | Latency (ms) | Connection Handling | False Positive Rate (%) | False Negative Rate (%) |
|---|---|---|---|---|---|
| Fortinet FortiGate 100F | 1000 | 5 | 1,000,000 | 1.5 | 0.2 |
| Palo Alto Networks PA-3220 | 800 | 6 | 500,000 | 1.0 | 0.3 |
| Cisco Firepower 2100 | 700 | 7 | 400,000 | 1.2 | 0.5 |
| SonicWall TZ Series | 600 | 8 | 300,000 | 1.8 | 0.4 |
This comparison assists organizations in assessing various firewall solutions while considering critical performance metrics, which can lead to more informed purchasing decisions.
Common Misconceptions About Firewalls
Many users hold misconceptions about firewalls that can lead to inadequate security measures. Firewalls are often seen as a catch-all solution for network security, but understanding their limitations is crucial for effective protection. This section aims to debunk prevalent myths surrounding firewalls and to highlight their true role in a comprehensive security strategy.
Myths Surrounding Firewalls
Despite their importance, there are several misconceptions about firewalls that can mislead users about their capabilities. Some of these include:
- Firewalls provide complete protection from all threats. Many believe that installing a firewall is sufficient for total security. However, firewalls primarily monitor and control incoming and outgoing traffic based on predetermined security rules; they do not detect all types of malware or insider threats.
- Firewalls are only necessary for businesses. There’s a common belief that firewalls are solely for corporate networks. In reality, home users also need firewalls to protect personal data and devices from unauthorized access and cyber threats.
- All firewalls are the same. Users often think that any firewall will perform equally well. In truth, firewalls vary significantly in terms of features and effectiveness, with some offering advanced threat detection and others lacking critical functionalities.
Risks of Relying Solely on Firewalls
Relying only on firewalls can create significant vulnerabilities within a network. While firewalls act as a barrier against certain types of traffic, they cannot address all forms of cyber threats.
- Limited Visibility: Firewalls often lack the ability to analyze encrypted traffic, which can hide malicious activities. Cybercriminals increasingly use encryption to bypass firewall controls, making it essential to pair firewalls with other security measures that inspect encrypted traffic.
- Insider Threats: Firewalls are typically designed to monitor outside traffic. They may not adequately address threats originating from within the organization, such as disgruntled employees or compromised user accounts.
- Vulnerable Endpoints: Devices within a network, such as smartphones, tablets, and IoT devices, may not have the same level of protection as the firewall itself. If these devices are compromised, they can serve as entry points for attackers, bypassing the firewall’s defenses.
Education on Firewall Limitations
Educating users about the limitations of firewall technology is vital for establishing a robust security posture. Awareness can empower users to adopt a multi-layered security approach.
- Training Sessions: Regular training can help users understand how firewalls work and their limitations. Practical demonstrations showing how threats can bypass firewalls can reinforce learning.
- Resource Distribution: Providing easy access to educational materials, such as articles and videos that explain network security in simple terms, can enhance understanding among employees and users.
- Encouraging Vigilance: Users should be encouraged to adopt good security habits, like using strong passwords and being cautious with email attachments and links, as these practices complement firewall protection.
“Firewalls are essential, but they are not the only line of defense. Comprehensive security requires a layered approach.”
Future Trends in Firewall Development
As the landscape of cybersecurity evolves, so too does the technology designed to protect networks. Firewalls are no longer just passive defenses; they are becoming intelligent systems that adapt to emerging threats. The convergence of various advanced technologies is expected to shape the future of firewall development significantly. This transformation will not only enhance their effectiveness but also broaden their application in various sectors.
The integration of artificial intelligence (AI) and machine learning (ML) into firewall technology is a key trend that is set to redefine how these systems operate. By leveraging vast amounts of data, AI and ML can enable firewalls to detect anomalies in real time and respond to threats more proactively. This evolution allows for a more dynamic approach to network security, making it possible to identify and neutralize potential risks before they can cause harm.
Emerging Technologies Influencing Firewalls
Several emerging technologies are anticipated to play a pivotal role in enhancing firewall capabilities:
- Quantum Computing: The advent of quantum computing may revolutionize encryption methods, enabling firewalls to process data at unprecedented speeds while enhancing security protocols.
- Internet of Things (IoT): As more devices connect to the internet, firewalls will need to adapt by integrating IoT security protocols to manage the increased traffic and protect against vulnerabilities specific to these devices.
- Blockchain Technology: The decentralized nature of blockchain can be used to enhance data integrity and security within firewalls, making it more challenging for unauthorized changes to occur.
The significance of these technologies cannot be understated, as they represent the forefront of innovation in cybersecurity. Organizations will increasingly adopt these technologies in tandem with firewalls to create robust security frameworks.
Artificial Intelligence and Machine Learning Enhancements
AI and ML are expected to notably enhance the functionality of firewalls in various ways:
- Automated Threat Detection: Firewalls equipped with AI can analyze vast datasets quickly, identifying patterns that signify potential threats with greater accuracy than traditional systems.
- Adaptive Security Responses: Machine learning algorithms enable firewalls to learn from past incidents, allowing them to automatically adjust their defensive strategies in response to new and evolving threats.
- Reduced False Positives: By improving the accuracy of threat detection, AI reduces the number of false positives, minimizing disruptions to legitimate traffic and ensuring a smoother user experience.
These enhancements position firewalls as proactive tools in the ongoing battle against cyber threats, shifting their role from mere defenders to active participants in network security.
Projections for Future Firewall Capabilities
Looking ahead, the capabilities of firewalls are projected to expand significantly, driven by technological advancements:
- Integration with Cloud Security: Future firewalls are likely to be designed with seamless integration into cloud infrastructures, providing consistent protection across hybrid environments.
- Behavioral Analysis: Firewalls will increasingly incorporate behavioral analytics to detect unusual activities and potential insider threats, thereby enhancing overall security posture.
- Enhanced User Interfaces: Future firewall solutions may feature more intuitive user interfaces that allow even non-technical users to manage security settings effectively, democratizing access to cybersecurity tools.
The trajectory for firewall development shows a clear movement towards not just enhanced security, but also greater usability and adaptability, aligning with the complex needs of modern organizations. As these technologies mature, firewalls will become more integrated and intelligent, setting new standards in network protection.
Last Recap
In summary, firewalls remain an indispensable component of any comprehensive security strategy, continuously evolving to meet the demands of modern cyber threats. As we look to the future, the integration of artificial intelligence and machine learning is poised to revolutionize firewall capabilities, making them smarter and more adaptive than ever. By prioritizing proper configuration and understanding the limitations of firewall technology, organizations can better protect their networks and maintain a secure digital environment.
Detailed FAQs
What is a firewall?
A firewall is a security device or software that monitors and controls incoming and outgoing network traffic based on predetermined security rules.
How does a firewall differ from antivirus software?
While firewalls protect networks by controlling traffic, antivirus software detects and removes malicious software from individual devices.
Can a firewall stop all cyber threats?
No, firewalls are not foolproof and should be part of a multi-layered security approach to effectively mitigate various cyber threats.
Are all firewalls the same?
No, there are different types of firewalls (hardware and software) with varying functionalities designed to address specific security needs.
How often should firewall rules be updated?
Firewall rules should be reviewed and updated regularly, especially in response to new security threats or changes in network configuration.