In today’s digital landscape, Cybersecurity emerges as a critical pillar that safeguards information and maintains trust in our interconnected world. As we increasingly rely on technology for personal and professional activities, the vulnerabilities that come with it also grow, making it essential to understand the nuances of protecting sensitive data. This exploration into Cybersecurity provides insights into its fundamental principles, the array of threats that exist, and the strategies necessary for effective defense.
From the core concepts of confidentiality, integrity, and availability to the evolving landscape of cyber threats, this discussion will illuminate the importance of being proactive in implementing cybersecurity measures. With an emphasis on technology’s role in defense mechanisms and the ethical considerations organizations must navigate, the journey through this topic promises to enhance your understanding of the vital role Cybersecurity plays in our lives.
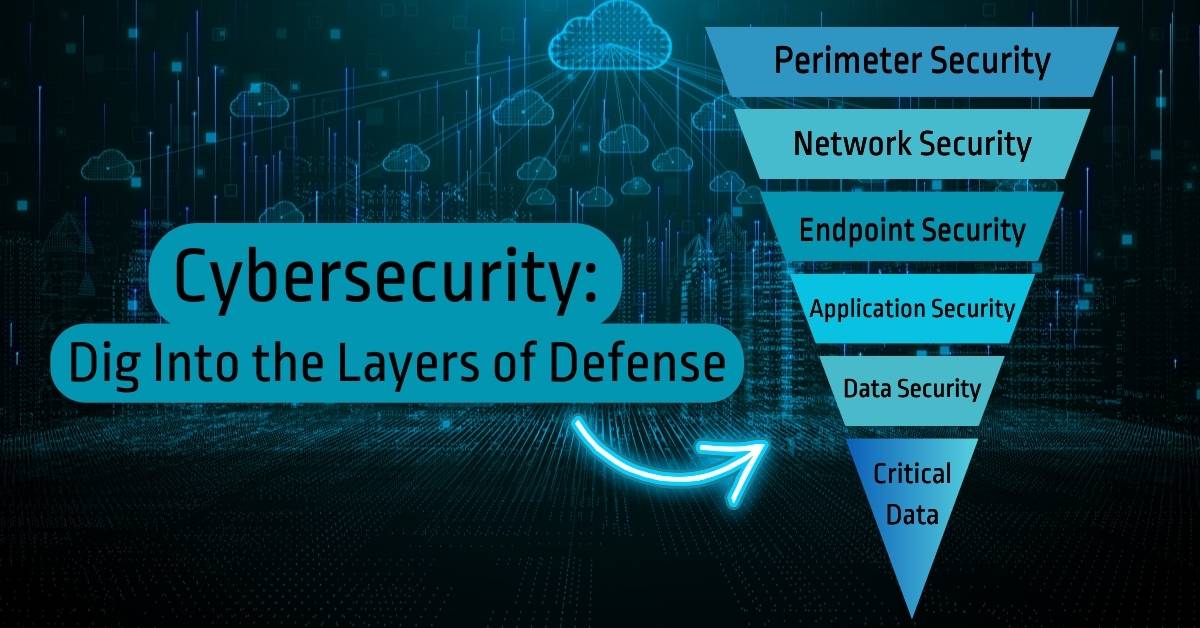
Understanding the Fundamental Concepts of Cybersecurity
In today’s digitally driven world, understanding the core principles of cybersecurity is essential for protecting sensitive information and maintaining operational integrity. The key concepts—confidentiality, integrity, and availability (often referred to as the CIA triad)—form the backbone of a robust cybersecurity framework. Organizations must comprehend these principles to defend against an ever-evolving landscape of cyber threats.
The principle of confidentiality ensures that sensitive information is accessible only to those authorized to view it. This is crucial for safeguarding personal data, trade secrets, and proprietary information. Techniques such as encryption and access controls are employed to uphold confidentiality. Integrity, on the other hand, guarantees that data remains accurate and unaltered unless changes are authorized. Implementing measures like checksums and hashing algorithms helps maintain data integrity. Finally, availability means that information and resources are accessible to authorized users when needed, often achieved through redundancy, failover systems, and regular maintenance.
Types of Cyber Threats and Their Potential Impacts
Understanding the various types of cyber threats is critical for organizations to effectively mitigate risks. Cyber threats can come in many forms, each with its own potential impact on businesses. The significance of recognizing these threats lies in the ability to implement appropriate defenses and response strategies.
- Malware: This includes viruses, worms, and Trojans that can corrupt or steal data. The impact can range from operational disruptions to significant financial losses.
- Phishing: Cyber attackers use deceptive emails to trick individuals into revealing personal information. Successful phishing campaigns can result in identity theft and unauthorized access to sensitive accounts.
- DDoS Attacks: Distributed Denial of Service attacks flood servers with excessive traffic, leading to outages. The repercussions can include loss of revenue and damaged reputation.
- Ransomware: This malware encrypts files and demands payment for decryption. The financial impact can be devastating, with organizations potentially facing heavy ransom fees and recovery costs.
Common Cybersecurity Terminologies and Their Definitions
Familiarity with cybersecurity terminology is vital for effective communication and understanding within the field. Here are some key terms that are frequently used:
- Firewall: A security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules.
- Intrusion Detection System (IDS): A device or software application that monitors network or system activities for malicious actions or policy violations.
- Encryption: The process of converting information or data into a code to prevent unauthorized access.
- Two-Factor Authentication (2FA): An additional layer of security that requires not only a password and username but also something that only the user has on them.
Understanding these foundational concepts and terms is essential for building a secure environment and fostering a culture of cybersecurity awareness within organizations.
Exploring the Different Types of Cybersecurity Threats
Cybersecurity threats continue to evolve, posing significant risks to individuals and organizations alike. Understanding the landscape of these threats is essential for implementing effective defenses. This section examines the most prevalent types of threats, their evolution over time, and notable real-world incidents that highlight their impact.
Prevalent Cybersecurity Threats
Among the myriad of cybersecurity threats, several have emerged as particularly damaging or disruptive. Below are some of the most significant threats that organizations face today:
- Phishing: Phishing attacks typically involve fraudulent emails or messages designed to trick individuals into revealing sensitive information like passwords or credit card numbers. These attacks have evolved from simple text-based emails to sophisticated campaigns that mimic legitimate communications from trusted entities.
- Malware: Malware, short for malicious software, encompasses a wide variety of harmful software, including viruses, worms, and trojans. Malware can steal data, damage systems, or provide unauthorized access to attackers. The proliferation of mobile devices has led to the rise of mobile malware, targeting users through applications and websites.
- Ransomware: Ransomware has gained notoriety for encrypting a victim’s files and demanding payment for the decryption key. Notable attacks, such as the Colonial Pipeline incident in 2021, showcased the potential for ransomware to disrupt critical infrastructure and draw public attention to cybersecurity vulnerabilities.
Evolution of Cyber Threats
The landscape of cyber threats has transformed dramatically over the past few decades. Initially, threats were often the work of individual hackers seeking notoriety. However, the motivations have shifted towards financial gain, political agendas, and even state-sponsored attacks. This evolution has introduced more complex and organized cybercrime.
The early 2000s saw the advent of worms and viruses that spread across networks, while the last decade has introduced advanced persistent threats (APTs) characterized by prolonged and targeted cyberattacks. Attackers now leverage sophisticated techniques, such as social engineering and artificial intelligence, to bypass traditional security measures.
Real-World Cyber Incidents
Several high-profile cyber incidents exemplify the severity and repercussions of cyber threats. These incidents not only illustrate the vulnerabilities present in various sectors but also underscore the need for robust cybersecurity measures.
- Yahoo Data Breach (2013-2014): One of the largest breaches in history, the Yahoo hack compromised the personal information of all 3 billion user accounts. The breach resulted in a significant loss of customer trust and a $350 million reduction in the sale price when Verizon acquired Yahoo.
- Target Data Breach (2013): In this incident, hackers accessed over 40 million credit and debit card numbers and 70 million customer records. Target faced not only substantial financial losses but also long-lasting reputational damage.
- WannaCry Ransomware Attack (2017): The WannaCry attack affected over 200,000 computers across 150 countries, disrupting critical services, including the UK’s National Health Service. The incident highlighted the importance of timely software updates and patch management.
Cybersecurity is not just an IT issue; it is a business issue that requires attention from all levels of an organization.
Implementing Effective Cybersecurity Strategies for Businesses
In today’s digital landscape, businesses face a multitude of cybersecurity threats that can compromise sensitive information, disrupt operations, and damage reputations. To navigate these challenges, it is essential to establish effective cybersecurity strategies that not only safeguard assets but also promote a culture of security awareness. This involves a comprehensive approach that includes risk management, incident response, and continuous education for employees.
Comprehensive Security Strategy Design
Designing a robust cybersecurity strategy begins with understanding the unique risks associated with your business environment. A comprehensive strategy should encompass two critical components: risk management and incident response. Risk management involves identifying vulnerabilities and potential threats, assessing their impact, and prioritizing actions to mitigate those risks effectively. Incident response Artikels the procedures to follow in the event of a security breach, ensuring a quick and efficient recovery.
To create a solid security strategy, consider the following steps:
- Conduct a thorough asset inventory to identify all information systems and data that require protection.
- Evaluate potential threats and vulnerabilities specific to your industry and technological environment.
- Develop risk mitigation strategies tailored to the identified threats, including technical measures and administrative policies.
- Establish an incident response team responsible for executing the response plan and managing communication during a breach.
- Implement continuous monitoring to detect and respond to security incidents in real-time.
Importance of Employee Training
Employee training is a cornerstone of any effective cybersecurity strategy. Human error remains one of the leading causes of security breaches; therefore, enhancing cybersecurity awareness among staff is vital. Regular training sessions equip employees with the knowledge to recognize phishing attempts, handle sensitive data securely, and adhere to best practices in cybersecurity.
Training programs should include:
- Workshops on recognizing social engineering tactics and phishing scams.
- Guidelines on creating strong passwords and utilizing multi-factor authentication.
- Simulated cyberattack scenarios to help staff practice their response to real threats.
- Policies outlining the proper use of company devices and data handling procedures.
- Regular updates on the latest cybersecurity trends and emerging threats.
Cybersecurity Risk Assessment Procedure
Conducting a cybersecurity risk assessment is a systematic process that helps identify and analyze the risks to an organization’s critical information assets. A well-structured risk assessment is essential for prioritizing security measures and allocating resources effectively.
Follow these steps to conduct a cybersecurity risk assessment:
- Identify assets: List all critical information assets, including hardware, software, data, and personnel.
- Determine threats: Identify potential threats to each asset, such as cyberattacks, natural disasters, or insider threats.
- Evaluate vulnerabilities: Assess each asset for vulnerabilities that could be exploited by identified threats.
- Assess impact: Analyze the potential impact of a successful attack on each asset, considering factors such as financial loss, reputational damage, and operational disruption.
- Prioritize risks: Rank the risks based on their likelihood and potential impact, allowing for informed decision-making regarding mitigation strategies.
- Develop a remediation plan: Create a plan outlining specific actions to address high-priority risks, including implementing technical controls, policies, and employee training.
“Cybersecurity is not just a technical issue; it is a business issue that requires a comprehensive strategy encompassing people, processes, and technology.”
The Role of Technology in Cybersecurity Defense Mechanisms
In today’s digital landscape, the importance of cybersecurity cannot be overstated. With increasing online threats, organizations are turning to a variety of technologies to defend their information systems. Understanding the role of these technologies is essential for building a robust defense strategy against cyber threats.
Cybersecurity tools employ various technologies to protect sensitive data, ensure privacy, and maintain the integrity of systems. The effectiveness of these technologies varies based on their application, the nature of the threats faced, and the specific environment in which they are deployed. A comprehensive security posture often requires the integration of multiple technologies to address the myriad of risks that organizations encounter.
Key Cybersecurity Technologies
Several fundamental technologies form the backbone of cybersecurity defenses. Each plays a vital role in preventing unauthorized access and mitigating potential threats. The following technologies are widely adopted in cybersecurity practices:
- Firewalls: Firewalls act as barriers between trusted networks and untrusted networks, filtering incoming and outgoing traffic based on predetermined security rules. They can be hardware-based, software-based, or a combination of both, and are crucial in blocking unauthorized access while allowing legitimate communication.
- Intrusion Detection Systems (IDS): IDS monitor network traffic for suspicious activity and known threats, alerting administrators to potential security breaches. They can be host-based or network-based, providing essential insights into the security posture of an organization’s network.
- Encryption: Encryption protects sensitive data by encoding it into a format that can only be read by authorized parties. This technology is essential for securing data at rest, in transit, or during processing, ensuring confidentiality and compliance with regulations.
- Antivirus and Anti-malware Software: These programs are designed to detect, prevent, and remove malicious software that could harm systems or compromise data integrity. Regular updates and scans are vital for maintaining effectiveness against evolving threats.
- Virtual Private Networks (VPNs): VPNs provide secure remote access to organizational networks by encrypting internet traffic and masking the user’s IP address. This technology is crucial for protecting sensitive information when employees work remotely or access resources over public networks.
Effectiveness of Security Tools
The effectiveness of security tools can vary significantly based on their deployment context and the specific threats they address. For instance, firewalls are highly effective in blocking unauthorized access but may not detect sophisticated threats that bypass these barriers. In contrast, IDS tools can identify unusual patterns but may generate false positives, requiring human intervention to validate alarms.
Additionally, the integration of multiple security tools enhances overall effectiveness. For example, combining firewalls with IDS and encryption creates layers of defense, making it more challenging for attackers to penetrate an organization’s security. Organizations must regularly assess their security landscape to determine the effectiveness of their tools and adjust accordingly.
Emerging Technologies in Cybersecurity
The rise of emerging technologies, particularly artificial intelligence (AI) and machine learning (ML), is transforming the cybersecurity landscape. AI and ML can analyze vast amounts of data at unprecedented speeds, identifying patterns and anomalies that human analysts may miss. These technologies enhance threat detection and response capabilities, enabling organizations to react swiftly to potential breaches.
For example, AI-driven security systems can learn from previous attacks, continuously improving their predictive capabilities. Machine learning algorithms can adapt to new threats in real-time, making them invaluable in combating sophisticated cyber attacks. Many organizations are now implementing AI in their cybersecurity strategies to stay ahead of potential threats.
“AI and ML technologies are reshaping the cybersecurity landscape, providing organizations with advanced tools to detect and respond to cyber threats more effectively.”
Overall, as cyber threats evolve, so too must the technologies we use to defend against them. Embracing a multi-layered approach that incorporates both established and emerging technologies will be crucial in safeguarding digital assets.
Legal and Ethical Considerations in Cybersecurity Practices
In the rapidly evolving landscape of technology, organizations are increasingly faced with a myriad of legal and ethical challenges in their cybersecurity practices. Adherence to regulations and compliance standards is not just a formality; it’s a critical component that safeguards both the organization and its stakeholders. Understanding these frameworks, alongside the ethical implications regarding data privacy and user consent, forms the backbone of responsible cybersecurity. This discussion will delve into significant regulations, ethical considerations, and relevant case studies to highlight the legal landscape surrounding cybersecurity.
Regulations and Compliance Standards
Organizations must navigate through a variety of regulations and compliance standards designed to protect sensitive data and ensure cybersecurity. These regulations often vary by country and industry but share common goals of safeguarding personal information and fostering trust. Compliance with these standards requires a proactive approach to data management and security.
- General Data Protection Regulation (GDPR): Enforced in the European Union, GDPR mandates strict guidelines on data processing and privacy, emphasizing user consent and the right to be forgotten.
- Health Insurance Portability and Accountability Act (HIPAA): In the healthcare sector, HIPAA imposes regulations to protect patient data, ensuring that organizations implement adequate security measures to safeguard sensitive information.
- Payment Card Industry Data Security Standard (PCI DSS): This standard is critical for organizations that handle credit card transactions, outlining security measures to protect cardholder data from breaches.
- Federal Information Security Management Act (FISMA): This U.S. legislation emphasizes the need for federal agencies to secure their information systems, requiring them to implement robust cybersecurity measures.
Ethical Considerations Regarding Data Privacy and User Consent
Ethics in cybersecurity encompasses the principles guiding organizations in their treatment of user data and privacy. Organizations must consider how they collect, store, and utilize user information, as well as the implications of these actions on stakeholder trust.
Organizations have a moral obligation to ensure that user consent is obtained clearly and transparently before collecting personal data.
In this context, ethical considerations include:
- Transparency: Users should be informed about what data is being collected, how it will be used, and whom it will be shared with.
- Informed Consent: Individuals should have the opportunity to provide explicit consent before their data is processed, with the ability to withdraw consent easily.
- Data Minimization: Organizations should collect only the data that is necessary for their purposes, avoiding unnecessary data accumulation.
- Accountability: Organizations must be held accountable for their data handling practices and must have measures in place to address data breaches and privacy violations.
Case Studies Illustrating Legal Consequences of Cybersecurity Breaches
Numerous high-profile cybersecurity breaches have resulted in significant legal consequences for organizations, highlighting the importance of compliance with regulations and ethical standards.
- Equifax Data Breach (2017): This incident exposed sensitive information of approximately 147 million consumers. Equifax faced multiple lawsuits and eventually agreed to pay up to $700 million in total settlements, underlining the repercussions of failing to secure user data.
- Target Data Breach (2013): The breach resulted in the theft of credit card information of over 40 million customers. Target incurred over $200 million in costs, including settlements and fines, emphasizing the need for robust cybersecurity measures.
- Yahoo Data Breach (2013-2014): The revelation that over 3 billion accounts were compromised led to a significant legal fallout, including a $350 million reduction in the sale price to Verizon, highlighting the financial impact of inadequate cybersecurity.
The Importance of Cybersecurity in a Remote Work Environment
The shift to remote work has transformed the way organizations operate, bringing flexibility and convenience. However, it has also introduced unique cybersecurity challenges that can jeopardize sensitive information and overall business operations. Understanding the importance of cybersecurity in a remote work environment is crucial for both employers and employees to maintain security and protect valuable data.
Remote work arrangements pose several challenges that can leave organizations vulnerable to cyber threats. Employees accessing sensitive company data from personal devices and unsecured networks increase the risk of data breaches. The lack of physical security in remote locations can make it harder to safeguard critical information, while employees may inadvertently fall prey to phishing attacks or malware due to decreased vigilance in a less controlled environment. Additionally, the rapid adoption of collaboration tools can lead to misconfigurations and unintended exposure of sensitive data if not properly managed.
Challenges of Remote Work on Cybersecurity
The remote work environment introduces various challenges that organizations must navigate to ensure cybersecurity. Understanding these challenges is essential for developing effective security measures. The following points highlight the key issues:
- Increased Attack Surface: With employees accessing systems from multiple locations and devices, the potential entry points for cyber attacks multiply.
- Unsecured Networks: Employees often connect to public Wi-Fi networks that lack sufficient security, making their connections susceptible to eavesdropping and man-in-the-middle attacks.
- Device Vulnerability: Personal devices may not have the same security measures as company-owned devices, increasing the risk of malware infections and data leaks.
- Human Error: The likelihood of security lapses can rise as employees juggle work and home responsibilities, leading to potential oversights like weak passwords and mishandling of sensitive data.
Best Practices for Securing Remote Work Setups
Implementing best practices is critical to mitigating the risks associated with remote work. Organizations should encourage employees to follow these guidelines:
- Use of VPNs: Utilizing a Virtual Private Network (VPN) encrypts internet traffic, protecting data from interception and ensuring secure access to company resources.
- Multi-Factor Authentication: Enforcing multi-factor authentication adds an extra layer of security, making it harder for unauthorized users to gain access even if credentials are compromised.
- Regular Software Updates: Keeping operating systems and applications up to date helps protect against vulnerabilities that cybercriminals could exploit.
- Security Awareness Training: Providing continuous training on recognizing phishing attempts and safe internet practices can empower employees to make informed decisions.
Tools and Solutions for Secure Remote Collaboration
To facilitate secure remote collaboration, organizations can leverage various tools and technologies designed to enhance security in a distributed workforce. Here are some effective solutions:
- Encryption Tools: Utilizing encryption for data storage and transmission protects sensitive information from unauthorized access.
- Secure File Sharing Platforms: Implementing platforms that offer secure file sharing with built-in access controls can prevent data leaks during collaboration.
- Endpoint Security Software: Deploying endpoint security solutions helps monitor and protect devices connected to the network from malware and unauthorized access.
- Collaboration Tools with Built-in Security: Using collaboration tools that prioritize security, such as end-to-end encryption and robust authentication measures, ensures safe communication and data sharing.
Building a Career in Cybersecurity
Cybersecurity is an ever-evolving field that offers numerous opportunities for those looking to build a fulfilling career. With the increasing frequency of cyber threats, the demand for skilled professionals continues to grow, making it an attractive choice for aspiring tech-savvy individuals. This guide Artikels the necessary skills, certifications, and career paths available within the cybersecurity domain.
Essential Skills and Certifications
To be successful in cybersecurity, individuals must develop a robust set of skills and obtain relevant certifications. Here are some key skills and certifications that can significantly enhance a professional’s career prospects:
- Technical Skills: Proficiency in networking, operating systems, and programming languages is critical. Familiarity with security protocols and encryption methods is also essential.
- Analytical Skills: The ability to analyze data and recognize patterns is crucial for identifying vulnerabilities and potential attacks.
- Problem-Solving Skills: Cybersecurity professionals must be adept at troubleshooting and developing solutions in real-time.
The following certifications are widely recognized and can bolster one’s credentials:
- CompTIA Security+: This entry-level certification covers foundational cybersecurity concepts.
- CISSP (Certified Information Systems Security Professional): Ideal for experienced professionals, this certification focuses on comprehensive security practices.
- CEH (Certified Ethical Hacker): This certification emphasizes the skills needed to think like a hacker to better defend against cyber threats.
Career Paths in Cybersecurity
The cybersecurity domain offers various career paths, each with unique responsibilities and requirements. Aspiring professionals can explore the following roles:
- Security Analyst: Focuses on monitoring and protecting an organization’s systems and networks. Requires a strong understanding of security tools and technologies.
- Penetration Tester: Simulates cyber attacks to identify vulnerabilities in systems. This role requires creativity and a solid grasp of hacking techniques and tools.
- Security Architect: Designs and implements security systems. This role demands extensive experience and knowledge of security frameworks.
Each role comes with its own education and experience requirements, often necessitating a combination of formal education, hands-on experience, and certifications.
Networking and Professional Development Opportunities
Building a career in cybersecurity also involves networking and continuous professional development. Engaging with the community can open doors and enhance knowledge. Here are some key avenues:
- Conferences and Workshops: Events such as Black Hat and DEF CON provide invaluable insights and networking opportunities with industry experts.
- Online Forums and Groups: Platforms like LinkedIn and specialized forums allow professionals to share knowledge, ask questions, and connect with potential mentors.
- Webinars and Online Courses: Continuous learning through webinars and specialized online courses helps professionals stay up-to-date with the latest trends and technologies.
Participating in these activities not only builds a professional network but also enhances skills and knowledge, which are vital in this fast-paced field.
Future Trends and Challenges in Cybersecurity
As the digital landscape evolves, the realm of cybersecurity faces an array of emerging threats and challenges. The rapid pace of technological advancements, particularly in areas such as the Internet of Things (IoT) and blockchain technology, significantly impacts how cybersecurity is approached. Understanding these trends is crucial for organizations aiming to safeguard their assets while adapting to new threats.
The cybersecurity landscape is increasingly defined by the convergence of various technologies that introduce both opportunities and vulnerabilities. The proliferation of connected devices through IoT expands the attack surface, while innovations like blockchain offer potential improvements in security protocols. However, these advancements also present unique challenges that organizations must address to maintain robust cybersecurity measures.
Emerging Cyber Threats and Challenges
The rise of sophisticated cyber threats necessitates organizations to stay vigilant and proactive. Several key challenges can be identified based on current trends:
- Increasing sophistication of cyberattacks: Attackers are leveraging advanced techniques such as AI and machine learning to enhance their methods, making it more challenging for traditional defenses to keep up.
- Supply chain vulnerabilities: As companies increasingly rely on third-party vendors, weaknesses within the supply chain can create significant entry points for attackers, making supply chain security a priority.
- Data privacy regulations: Stricter data protection laws are being implemented globally, compelling organizations to enhance their compliance measures and increase accountability in handling sensitive information.
- Shortage of cybersecurity professionals: The demand for skilled cybersecurity experts continues to outpace supply, leading to gaps in security teams that can be exploited by malicious actors.
Impact of IoT and Blockchain on Cybersecurity
The integration of IoT devices in everyday life has revolutionized connectivity, but it has also introduced numerous security challenges. Each connected device represents a potential entry point for cybercriminals, necessitating the implementation of robust security measures.
In contrast, blockchain technology presents an opportunity to enhance cybersecurity through decentralized data storage and enhanced encryption. The immutable nature of blockchain can secure transactions and protect against unauthorized access. However, its complexity and the nascent state of its deployment create a learning curve concerning its security implications.
The implications of these technologies can be summarized as follows:
- IoT devices require stringent security protocols, including regular updates and strong authentication methods, to mitigate risks of unauthorized access.
- Blockchain can enhance security by offering transparent transaction records and reducing reliance on centralized databases, but it also poses challenges for scalability and interoperability with existing systems.
- Effective security frameworks must evolve to address the unique vulnerabilities posed by the integration of IoT and blockchain technologies, ensuring comprehensive protection across all digital assets.
Predictions for Cybersecurity Innovations
Looking ahead, several innovations are anticipated to shape the future of cybersecurity. A few notable predictions include:
- Increased use of artificial intelligence (AI): AI-driven cybersecurity tools will become commonplace, enabling organizations to detect and respond to threats in real-time by analyzing vast amounts of data.
- Zero Trust security models: The adoption of Zero Trust frameworks, which operate on the principle of ‘never trust, always verify,’ will gain traction as organizations seek to minimize risk in a landscape characterized by remote work and cloud environments.
- Enhanced biometric security measures: Advances in biometric authentication methods, such as facial recognition and fingerprint scanning, will provide an additional layer of security while improving user experience.
- Decentralized security solutions: As blockchain technology matures, decentralized security solutions may emerge, providing innovative ways to protect data without relying on central authorities.
“The future of cybersecurity will be defined by the balance between innovation and the need for security; organizations that prioritize security will thrive in an increasingly complex digital landscape.”
Final Wrap-Up
As we conclude this exploration of Cybersecurity, it’s evident that maintaining a secure digital environment is a multifaceted endeavor, requiring vigilance, knowledge, and adaptation to new challenges. The importance of effective strategies, employee training, and the integration of advanced technologies cannot be overstated. As we move forward, embracing these principles will not only help protect individuals and organizations but also foster a safer digital landscape for everyone.
Query Resolution
What is Cybersecurity?
Cybersecurity refers to the practices and technologies that protect systems, networks, and data from cyber threats and unauthorized access.
Why is Cybersecurity important?
It is crucial because it helps prevent data breaches, protects sensitive information, and maintains the integrity and availability of systems.
What are common types of cyber threats?
Some common threats include phishing, malware, ransomware, and denial-of-service attacks.
How often should businesses conduct a cybersecurity risk assessment?
Businesses should conduct risk assessments regularly, at least annually, or whenever there are significant changes to their systems or operations.
What is the role of employee training in Cybersecurity?
Employee training is essential as it raises awareness about potential threats and educates staff on best practices to prevent security incidents.
What technologies are commonly used in Cybersecurity?
Common technologies include firewalls, intrusion detection systems, encryption, and antivirus software.