Encryption is a fundamental force in the digital age, acting as a guardian of our private communications and sensitive data. It transforms readable information, known as plaintext, into an unreadable format, or ciphertext, using complex algorithms and keys. This process is vital not just for individual users but also for businesses, as it secures transactions, protects intellectual property, and maintains confidentiality across various platforms. Everyday applications, such as messaging apps and online banking, rely on encryption to ensure that our personal information remains safe from prying eyes.
Understanding the basic concepts of encryption equips us with the knowledge to appreciate its critical role in modern communication. As we delve deeper, we will explore various encryption methods, their implementations in cybersecurity, and the legal and ethical dimensions surrounding their use. The future of encryption technology promises new advancements, but it also presents challenges that organizations must navigate.
Understanding the Basic Concepts of Encryption
Encryption is a critical technology in today’s digital age, serving as a cornerstone for secure communication. As the world becomes increasingly reliant on online interactions, protecting sensitive data from unauthorized access has never been more important. Encryption involves transforming readable information into an unreadable format, ensuring that only authorized parties can access the original message. This technology not only safeguards personal data but also plays a vital role in maintaining privacy and security in various sectors, including finance, healthcare, and government communications.
Encryption operates on several fundamental principles, encompassing a variety of terms and processes. The core components of encryption include plaintext, ciphertext, keys, and algorithms. Plaintext refers to the original, readable data or message that needs protection. When plaintext is processed through an encryption algorithm using a specific key, it is transformed into ciphertext, which is the scrambled version of the original data that appears meaningless to anyone who intercepts it. The key is a critical element in this process; it is a piece of information used by the algorithm to encrypt and decrypt the data. Without the correct key, it is nearly impossible to revert the ciphertext back to plaintext.
Algorithms dictate how data is transformed during the encryption process. There are various encryption algorithms, including symmetric encryption (where the same key is used for both encryption and decryption) and asymmetric encryption (which employs a pair of keys: a public key for encryption and a private key for decryption). Common examples of encryption in everyday applications include the use of HTTPS for secure online browsing, securing email communications through services like PGP (Pretty Good Privacy), and protecting sensitive files with software like VeraCrypt. Additionally, mobile banking apps use encryption to secure transactions and user data, ensuring that financial information remains confidential and safe from cyber threats.
The Different Types of Encryption Methods
Encryption plays a crucial role in safeguarding sensitive information in today’s digital age. It ensures data confidentiality, integrity, and authenticity while transmitting or storing information. Understanding the various encryption methods is essential for implementing effective security measures. The two primary types of encryption are symmetric and asymmetric encryption, each with distinct characteristics and applications.
Symmetric and Asymmetric Encryption
Symmetric encryption utilizes a single key for both encryption and decryption processes. This means that the sender and receiver must share the same secret key, which could pose a security risk if the key is intercepted. Common symmetric encryption algorithms include Advanced Encryption Standard (AES) and Data Encryption Standard (DES). Symmetric encryption is widely used for scenarios requiring fast processing speeds, such as encrypting data at rest or during point-to-point communication.
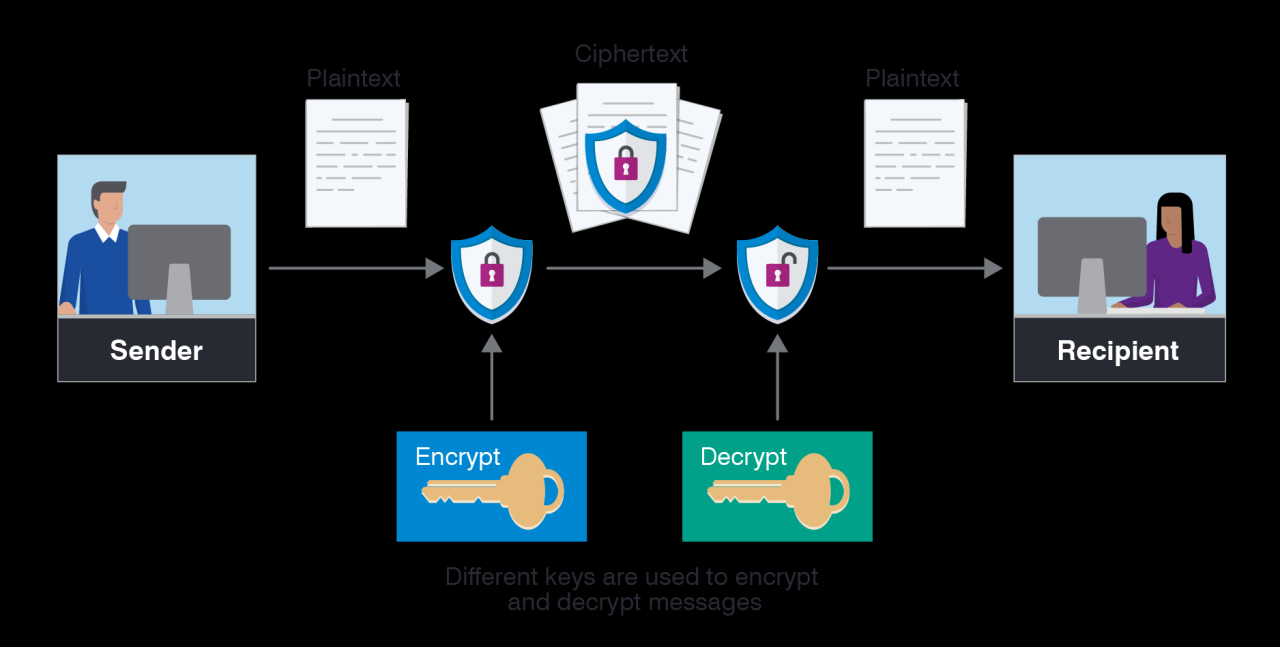
In contrast, asymmetric encryption employs a pair of keys: a public key for encryption and a private key for decryption. This method allows users to communicate securely without needing to share a secret key. One prominent example of asymmetric encryption is the RSA algorithm, which is commonly used for secure data transmission, digital signatures, and certificates. Asymmetric encryption, while generally slower than symmetric encryption, enhances security during key exchange, making it a preferred option for secure communications over the internet.
Encryption Algorithms
Several encryption algorithms exemplify the differences between symmetric and asymmetric methods, each suited for specific use cases. Understanding these algorithms is crucial for selecting the right encryption strategy.
- AES (Advanced Encryption Standard): AES is a symmetric encryption algorithm widely adopted for its speed and strength. It supports key sizes of 128, 192, and 256 bits, providing robust security. AES is commonly used in applications like file encryption, VPNs, and securing sensitive data in cloud storage.
- RSA (Rivest-Shamir-Adleman): RSA is an asymmetric encryption algorithm that relies on the mathematical properties of prime numbers. It is extensively used in secure data transmission over the internet, particularly in establishing secure connections through SSL/TLS protocols.
- DES (Data Encryption Standard): DES, an older symmetric algorithm, uses a 56-bit key. While it was widely used in the past, advances in computational power have rendered it less secure. It is now mostly replaced by AES but may still be encountered in legacy systems.
Comparison of Encryption Methods
Below is a comparison table outlining the advantages and disadvantages of both symmetric and asymmetric encryption methods. This overview helps to illustrate when each type may be most effective in real-life applications.
| Type of Encryption | Advantages | Disadvantages |
|---|---|---|
| Symmetric Encryption | Faster processing, lower computational overhead, suitable for bulk data encryption. | Key distribution challenges, vulnerable if the key is intercepted. |
| Asymmetric Encryption | Enhanced security during key exchange, eliminates the need for secret key sharing. | Slower than symmetric encryption, more computationally intensive. |
The Role of Encryption in Cybersecurity

Encryption is a fundamental aspect of modern cybersecurity practices, serving as a vital safeguard for sensitive data across various forms, whether at rest, in transit, or in use. By converting information into a coded format that can only be accessed by authorized users, encryption provides a robust line of defense against data breaches and unauthorized access. In an era where cyber threats are increasingly sophisticated, the role of encryption cannot be overstated; it not only protects individual privacy but also helps organizations maintain their integrity and trustworthiness in the digital landscape.
The contribution of encryption to an organization’s security posture is multi-faceted. Firstly, it acts as a barrier against data breaches by ensuring that even if unauthorized parties manage to access sensitive data, the information remains unreadable without the correct decryption keys. This is particularly crucial for organizations handling personal, financial, and proprietary information. Furthermore, encryption aids in regulatory compliance, as many industries are mandated to protect sensitive information using strong encryption methods. Failure to implement encryption can lead to significant legal and financial penalties, as well as reputational damage. Companies that neglect encryption are essentially leaving the door open for cybercriminals, exposing themselves to risks of theft, manipulation, and loss of consumer trust.
Industries Reliant on Encryption for Data Protection
Certain industries rely heavily on encryption to safeguard sensitive information due to their inherent risks and regulatory requirements. The following sectors exemplify this reliance:
- Healthcare: The protection of patient data under regulations like HIPAA necessitates robust encryption methods to ensure confidentiality and integrity.
- Finance: Financial institutions utilize encryption to secure transactions and protect sensitive account information from fraud and identity theft.
- Telecommunications: Encryption is crucial for safeguarding communication and protecting user data in an increasingly interconnected world.
- Government: National security agencies employ encryption to protect classified information from espionage and cyber attacks.
- E-commerce: Online retailers implement encryption to secure payment transactions and protect customer data from breaches.
The implications of not utilizing encryption extend beyond immediate financial loss; they can also include long-term damage to reputation, loss of customer trust, and a decrease in competitive advantage. As cyber threats continue to evolve, the importance of encryption as a critical component of an organization’s cybersecurity strategy grows ever more apparent.
Legal and Ethical Considerations of Encryption
The intersection of encryption technology with legal and ethical frameworks presents a complex landscape for businesses and individuals alike. As encryption becomes more integral to protecting sensitive information, understanding the regulations and ethical dilemmas it entails is crucial. Different jurisdictions have varied approaches to encryption laws, which can significantly impact how businesses operate across borders.
Regulations Surrounding Encryption in Different Jurisdictions
Encryption regulations differ widely across the globe, directly influencing international business practices. In the United States, encryption is regulated under the Export Administration Regulations (EAR), which impose restrictions on the export of encryption technology, particularly to countries deemed national security threats. Meanwhile, the Federal Bureau of Investigation (FBI) has often advocated for “backdoor” access to encrypted communications, raising concerns about user privacy and security.
In the European Union, the General Data Protection Regulation (GDPR) has established stringent guidelines surrounding data protection, including the use of encryption as a protective measure. GDPR mandates that organizations implement appropriate security measures, including encryption, to safeguard personal data. Non-compliance can lead to heavy fines, impacting businesses significantly.
Here are some notable regulations and their implications:
- United States: Encryption exports are tightly controlled, affecting international sales and partnerships.
- European Union: GDPR requires encryption for personal data, enhancing user trust but imposing compliance costs on businesses.
- China: The Cybersecurity Law mandates that companies store user data locally and allows government access, challenging international firms’ encryption policies.
The contrasting regulatory environments illustrate the need for businesses to navigate carefully, as failure to comply can result in severe penalties and reputational damage.
Ethical Dilemmas of Encryption: Privacy Versus Security
The ethical implications of encryption present a significant tension between privacy rights and national security interests. On one side, encryption serves as a crucial safeguard for individual privacy, protecting sensitive information from unauthorized access. On the other hand, law enforcement agencies argue that unrestricted encryption can hinder investigations and national security efforts.
This dilemma was notably highlighted in the case of Apple vs. FBI in 2016, where the FBI sought access to the encrypted data of a terrorist’s iPhone. Apple refused, citing the need to protect user privacy and the potential risks of creating a backdoor. This case sparked a national debate on the balance between individual rights and collective security.
“The challenge lies in finding the right equilibrium where privacy is respected without compromising security.”
Other high-profile cases, such as the WhatsApp encryption debates and the ongoing discussions around the UK’s Investigatory Powers Act, further exemplify the challenges and complexities of encryption ethics. As society progresses, these discussions will continue to shape the future of encryption laws and ethical considerations.
The Future of Encryption Technology
As we dive into the future of encryption technology, we find ourselves at a crossroads of innovation and challenges. With the rise of emerging technologies like quantum computing and blockchain integration, the landscape of encryption is rapidly evolving. These advancements promise increased security and new methodologies, yet they also introduce complexities that organizations must navigate to remain secure.
Emerging Trends in Encryption
Two of the most significant trends influencing the future of encryption are quantum encryption and blockchain technologies. Quantum encryption leverages the principles of quantum mechanics to create virtually unbreakable encryption methods. For instance, Quantum Key Distribution (QKD) enables two parties to exchange encryption keys securely, ensuring that any attempt to intercept the communication is detectable. This innovation presents a formidable line of defense against cyber adversaries.
On the other hand, blockchain integration offers decentralized storage of encrypted data, enhancing security through distributed ledger technology. Organizations can use blockchain to ensure that data remains immutable and verifiable, which is critical in sectors like finance and healthcare. Consider how cryptocurrencies exemplify this innovation, where every transaction is encrypted and recorded across a distributed network, reducing the risks associated with centralized databases.
Challenges Facing Encryption Technology
While the future looks promising, encryption technology faces several potential challenges that could hinder its effectiveness over the next decade. One significant concern is the rapid advancement of decryption technologies, particularly with quantum computers capable of breaking traditional encryption methods. As organizations adopt new encryption solutions, they must also prepare for potential vulnerabilities arising from these advanced computational capabilities.
Moreover, regulatory changes can impact encryption practices significantly. Stricter compliance requirements may necessitate the use of specific encryption standards, posing challenges for organizations to balance security with operational flexibility. This regulatory landscape can lead to inconsistencies in how encryption is implemented across different industries.
Preparing for Evolving Threats
As encryption methods evolve, so do the threats they must counteract. To prepare, organizations should adopt a proactive approach to encryption by implementing adaptive and layered security measures. This includes regularly updating encryption algorithms to safeguard against emerging threats, conducting periodic security audits, and investing in employee training to recognize potential phishing or cyber-attack attempts.
Importantly, organizations should also consider collaboration with industry peers to share insights and develop best practices for encryption. By fostering a community of knowledge-sharing, organizations can stay ahead of potential risks and leverage collective expertise to enhance their encryption strategies.
“The future of encryption is not just about securing data; it’s about fortifying trust in a digital world.”
Practical Steps to Implement Encryption in Your Organization
Implementing encryption in your organization is a crucial step towards safeguarding sensitive information. With cyber threats on the rise, encryption serves as a powerful tool to protect data at rest and in transit. Here’s a structured approach to effectively implement encryption practices.
Step-by-Step Guide to Implement Encryption
To ensure a smooth encryption rollout, organizations can follow these practical steps:
- Assess Your Data: Identify what data needs protection—personal information, financial records, intellectual property, etc.
- Select the Right Encryption Tools: Choose tools based on your needs. For file encryption, consider tools like VeraCrypt; for email, use PGP or S/MIME.
- Develop Encryption Policies: Create clear policies outlining what data must be encrypted and the encryption standards to follow.
- Train Employees: Conduct training sessions for your staff to ensure they understand the importance of encryption and how to use the tools effectively.
- Implement Encryption: Start with the most sensitive data and gradually expand to include all necessary information.
- Regularly Review and Update: Encryption is not a one-time task. Regularly review your encryption practices and update them as needed to address new threats.
Types of Encryption Tools and Their Applications
Different encryption tools cater to specific needs within an organization. Understanding their applications is crucial for effective implementation.
- File Encryption Tools: Tools like BitLocker or VeraCrypt encrypt files and folders, protecting data on hard drives and removable media.
- Email Encryption: PGP and S/MIME provide secure email communications, ensuring that messages are only accessible to intended recipients.
- Database Encryption: Solutions such as SQL Server Transparent Data Encryption secure sensitive data in databases.
- VPN Services: Virtual Private Networks encrypt internet traffic, providing secure access to organizational resources remotely.
Case Studies of Successful Encryption Implementation
Several organizations have effectively implemented encryption, showcasing its importance across different sectors:
In a healthcare setting, a hospital encrypted patient records to comply with HIPAA regulations, significantly reducing data breaches.
A financial institution adopted end-to-end encryption for transactions, which not only protected customer data but also enhanced trust among users.
A government agency implemented disk encryption on all workstations, ensuring classified information remained secure from unauthorized access.
Common Misconceptions about Encryption
Encryption is often surrounded by myths that can mislead individuals and organizations alike. Understanding the true nature of encryption is vital in fostering robust security practices. Let’s explore some of the most prevalent misconceptions that can undermine effective encryption strategies.
Prevalent Myths about Encryption
Numerous misconceptions about encryption can lead to inadequate security measures. Here are five common myths debunked:
– Myth 1: Encryption is only for large organizations.
The belief that only large corporations need encryption can be dangerous. In reality, small businesses and individuals are equally at risk of data breaches. Encrypting sensitive information is essential for everyone.
– Myth 2: Encryption guarantees complete security.
While encryption significantly enhances security, it does not provide absolute protection. Vulnerabilities can arise from poor password management, outdated software, or human error, making layered security measures necessary.
– Myth 3: Encrypted data is unreadable to everyone.
Encrypting data does not mean it is unreadable to authorized users. Proper decryption keys allow access to encrypted information, which highlights the importance of protecting these keys from unauthorized access.
– Myth 4: All encryption methods are equally secure.
Not all encryption technologies offer the same level of security. Some older algorithms, like DES, are outdated and can be easily cracked. It is crucial to use strong, up-to-date encryption standards.
– Myth 5: Encryption slows down systems significantly.
Though encryption can introduce some latency, advancements in technology have minimized this impact. The benefits of securing data far outweigh potential performance issues.
These misconceptions can foster poor security practices, such as neglecting encryption altogether or relying on outdated methods, ultimately exposing sensitive information to threats.
To counter these misconceptions and improve security posture, consider the following best practices:
– Regularly update encryption methods to stay ahead of evolving threats.
– Implement strong access controls to protect encryption keys.
– Educate employees about the importance of encryption and security protocols.
– Perform regular security audits to identify potential vulnerabilities.
– Utilize comprehensive security solutions that include encryption as one layer of a multi-faceted approach.
By addressing these misconceptions and adhering to best practices, organizations can significantly enhance their data security.
The Relationship Between Encryption and Data Privacy
Encryption serves as a cornerstone for safeguarding personal information and sensitive data, establishing a crucial link between encryption technologies and data privacy regulations. With the growing emphasis on protecting consumer privacy, regulations like the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) have emerged, mandating organizations to secure users’ personal data. Encryption not only helps in compliance with these regulations but also enhances trust between consumers and businesses.
Encryption plays a vital role in ensuring compliance with data privacy regulations, primarily by providing a method to protect personal data from unauthorized access. Under GDPR, organizations are required to implement appropriate technical and organizational measures to ensure a level of security appropriate to the risk. This includes the use of encryption to safeguard data during storage and transmission. Similarly, CCPA emphasizes the need for companies to implement reasonable security procedures and practices to protect personal information. By employing encryption, organizations can reduce the risks of data breaches, which can lead to severe penalties under these regulations.
Leveraging Encryption for Personal Privacy Protection
Individuals can take actionable steps to utilize encryption to enhance their online privacy. Understanding the different methods of encryption and how they can be applied is essential for personal data protection. Here are some practical ways to implement encryption for safeguarding personal information:
- Use Encrypted Communication Tools: Opt for messaging apps that offer end-to-end encryption, such as Signal or WhatsApp. This ensures that only the sender and receiver can read the messages, preventing any third-party access.
- Enable Full-Disk Encryption: Activate full-disk encryption on your devices. This feature ensures that all data stored on the device is encrypted, making it inaccessible without the correct password or key.
- Secure Your Emails: Utilize email encryption services like PGP (Pretty Good Privacy) or S/MIME to encrypt your emails. This protects the content of your emails from prying eyes during transmission.
- Use a Virtual Private Network (VPN): A VPN encrypts your internet traffic, making it difficult for hackers and other entities to monitor your online activities and data transmissions.
- Backup Encrypted Data: Ensure that any backups of your sensitive data are also encrypted. This adds a layer of protection in case of accidental data loss or theft.
“Encryption is not just a technology; it is a fundamental principle of data privacy that empowers individuals and organizations to protect sensitive information.”
By following these practices, individuals can effectively leverage encryption to maintain their privacy online, aligning their actions with the principles Artikeld in regulations like GDPR and CCPA. Keeping data secure isn’t just a compliance issue; it’s a personal responsibility to protect one’s own digital footprint in an increasingly interconnected world.
Conclusion
In summary, encryption is not just a technical necessity; it is a cornerstone of trust in our digital interactions. As we’ve discussed, its various methods play a vital role in protecting sensitive information across numerous industries. With the evolving landscape of technology and threats, it is essential that organizations and individuals alike understand and implement effective encryption practices. By doing so, they can safeguard their data and privacy against potential breaches, ensuring a secure digital future.
Answers to Common Questions
What is encryption?
Encryption is the process of converting information into a secure format that cannot be easily read by unauthorized users.
How does encryption work?
Encryption works by using algorithms and keys to transform plaintext into ciphertext, making it unreadable without the correct key to decrypt it.
What is the difference between symmetric and asymmetric encryption?
Symmetric encryption uses the same key for both encryption and decryption, while asymmetric encryption uses a pair of keys — a public key for encryption and a private key for decryption.
Can encryption be broken?
While encryption can theoretically be broken, strong encryption methods are designed to be practically unbreakable with current technology and resources.
Do I need to encrypt my personal data?
Yes, encrypting personal data helps protect it from unauthorized access and breaches, especially when sharing sensitive information online.